Huawei H12-891_V1.0-ENU Übungsprüfungen
Zuletzt aktualisiert am 08.03.2026- Prüfungscode: H12-891_V1.0-ENU
- Prüfungsname: HCIE-Datacom V1.0
- Zertifizierungsanbieter: Huawei
- Zuletzt aktualisiert am: 08.03.2026
As shown in the figure, the stateful inspection firewall will forward the packet because the packet conforms to the firewall session state.
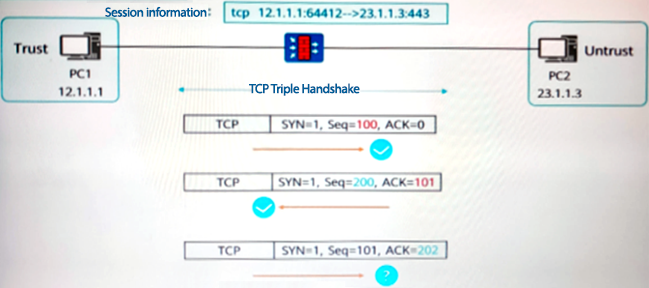
- A . True
- B . False
IP Source Guard (IPSG) is a source IP address filtering technology based on Layer 3 interfaces. It can prevent malicious hosts from forging the IP addresses of legitimate hosts to impersonate legitimate hosts, and also ensures that unauthorized hosts cannot Access the network or attack the network by specifying your own IP address.
- A . True
- B . False
Which of the following descriptions of the advantages of SR-MPLS are correct? (Multiple choice)
- A . SR-MPLS simplifies the control plane of MPLS networks
- B . SR-MPLS provides efficient TI-LFA FRR protection to achieve rapid recovery from path failures.
- C . SR-MPLS supports both traditional networks and SDN networks, is compatible with existing equipment, and ensures smooth evolution of existing networks to SDN networks.
- D . SR-MPLS intermediate nodes do not need to maintain path information, and there is less pressure on the device control layer.
Telemetry network models are divided into broad and narrow senses. What modules does broad Telemetry include? (Multiple choice)
- A . Equipment
- B . Analyzer
- C . Controller
- D . collector
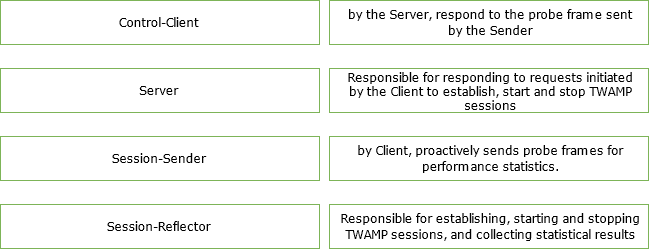
The TWAMP communication model includes Session – Sender, Session-Reflector, Control-Client and Server. Please match the functional modules with the corresponding descriptions.
When using DHCP Option 148 to deploy a switch, the DHCP server will not provide which of the following information to the switch to be deployed?
- A . Port number of the cloud management platform
- B . The port number of the device to be deployed
- C . IP address of the cloud management platform
- D . The IP address of the device to be deployed
MACsec can provide users with secure MAC layer data sending and receiving services.
Which of the following items are not among the services provided by MACsec?
- A . Integrity check
- B . Controllability check
- C . User data encryption
- D . Data source authenticity verification
What are the risks in the communication process of HTTP protocol? (Multiple choice)
- A . Eavesdropping risk: third parties can learn the content of communications
- B . Pretending: A third party can pretend to be someone else to participate in communications
- C . Risk of loss (Losing): Communication content may be lost with a small probability during transmission.
- D . Tampering risk (tampering): A third party can modify the communication content
What are the following advantages of GRE tunnel? (Multiple choice)
- A . The GRE tunnel expands the working scope of hop-limited network protocols and supports enterprises to flexibly design network topologies.
- B . GRE tunnel can be used to build a VPN network
- C . GRE tunnel can encapsulate ARP messages
- D . GRE tunnel can encapsulate multicast data
Which of the following descriptions of BGP/MPLSIPVPN routing interactions is wrong?
- A . PE and CE exchange IPv4 routing information.
- B . The egress PE can send IPv4 routes to the remote CE through BGP, IGP or static routing.
- C . The ingress PE changes the IPv4 routes received from the CE into VPNv4 routes and saves them according to different VPN instances.
- D . After receiving the VPNv4 routes advertised by the ingress PE, the egress PE filters the VPNv4 routes based on the RT attributes carried by the routes.

