ISA ISA-IEC-62443 Übungsprüfungen
Zuletzt aktualisiert am 08.03.2026- Prüfungscode: ISA-IEC-62443
- Prüfungsname: ISA/IEC 62443 Cybersecurity Fundamentals Specialist
- Zertifizierungsanbieter: ISA
- Zuletzt aktualisiert am: 08.03.2026
What are the four main categories for documents in the ISA-62443 (IEC 62443) series?
Available Choices (select all choices that are correct)
- A . General. Policies and Procedures. System, and Component
- B . End-User, Integrator, Vendor, and Regulator
- C . Assessment. Mitigation. Documentation, and Maintenance
- D . People. Processes. Technology, and Training
Which is the PRIMARY objective when defining a security zone?
Available Choices (select all choices that are correct)
- A . All assets in the zone must be from the same vendor.
- B . All assets in the zone must share the same security requirements.
- C . All assets in the zone must be at the same level in the Purdue model.
- D . All assets in the zone must be physically located in the same area.
Which of the following is an activity that should trigger a review of the CSMS?
Available Choices (select all choices that are correct)
- A . Budgeting
- B . New technical controls
- C . Organizational restructuring
- D . Security incident exposing previously unknown risk.
Which of the following is an example of separation of duties as a part of system development and maintenance?
Available Choices (select all choices that are correct)
- A . Changes are approved by one party and implemented by another.
- B . Configuration settings are made by one party and self-reviewed using a checklist.
- C . Developers write and then test their own code.
- D . Design and implementation are performed by the same team.
Which of the following is an industry sector-specific standard?
Available Choices (select all choices that are correct)
- A . ISA-62443 (EC 62443)
- B . NIST SP800-82
- C . API 1164
- D . D. ISO 27001
Which organization manages the ISA Secure conformance certification program?
Available Choices (select all choices that are correct)
- A . American Society for Industrial Security
- B . Automation Federation
- C . National Institute of Standards and Technology
- D . Security Compliance Institute
Which of the following is a recommended default rule for IACS firewalls?
Available Choices (select all choices that are correct)
- A . Allow all traffic by default.
- B . Allow IACS devices to access the Internet.
- C . Allow traffic directly from the IACS network to the enterprise network.
- D . Block all traffic by default.
Security Levels (SLs) are broken down into which three types?
Available Choices (select all choices that are correct)
- A . SL-1, SL-2, and SL-3
- B . Target.capability, and achieved
- C . Target.capability, and availability
- D . Target.capacity, and achieved
Using the risk matrix below, what is the risk of a medium likelihood event with high consequence?
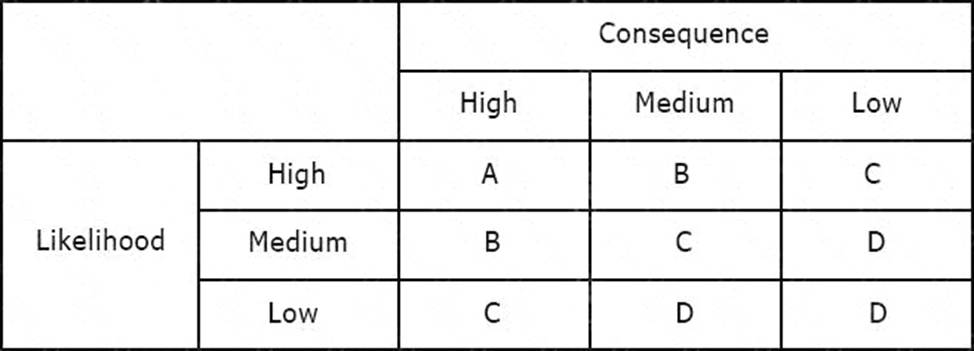
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which analysis method is MOST frequently used as an input to a security risk assessment?
Available Choices (select all choices that are correct)
- A . Failure Mode and Effects Analysis
- B . Job Safety Analysis
- C . Process Hazard Analysis (PHA)
- D . System Safety Analysis(SSA)
