CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
A disgruntled open-source developer has decided to sabotage a code repository with a logic bomb that will act as a wiper.
Which of the following parts of the Cyber Kill Chain does this act exhibit?
- A . Reconnaissance
- B . Weaponization
- C . Exploitation
- D . Installation
A company is aiming to test a new incident response plan. The management team has made it clear that the initial test should have no impact on the environment. The company has limited resources to support testing.
Which of the following exercises would be the best approach?
- A . Tabletop scenarios
- B . Capture the flag
- C . Red team vs. blue team
- D . Unknown-environment penetration test
A security analyst is reviewing the network security monitoring logs listed below:
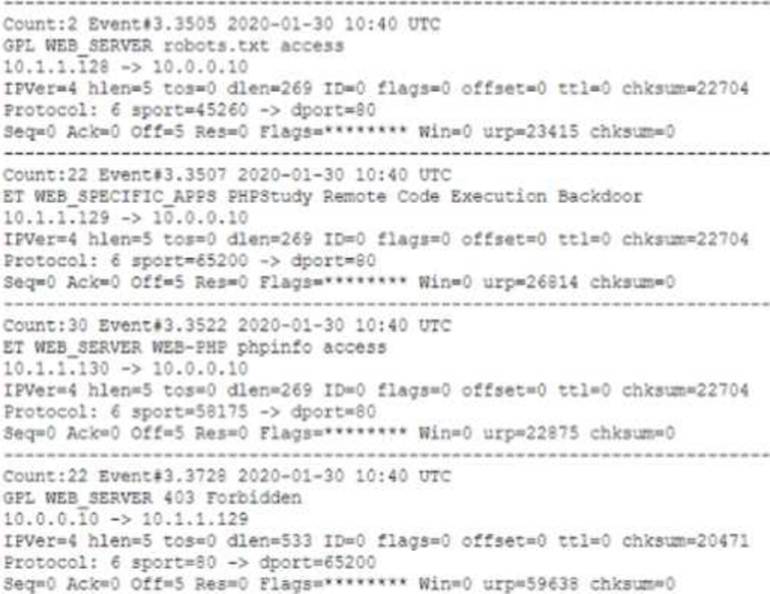
Which of the following is the analyst most likely observing? (Select two).
- A . 10.1.1.128 sent potential malicious traffic to the web server.
- B . 10.1.1.128 sent malicious requests, and the alert is a false positive
- C . 10.1.1.129 successfully exploited a vulnerability on the web server
- D . 10.1.1.129 sent potential malicious requests to the web server
- E . 10.1.1.129 can determine mat port 443 is being used
- F . 10.1.1.130 can potentially obtain information about the PHP version
An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on it infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host.
Which of the following data sources would most likely reveal evidence of the root cause? (Select two).
- A . Creation time of dropper
- B . Registry artifacts
- C . EDR data
- D . Prefetch files
- E . File system metadata
- F . Sysmon event log
A SOC analyst identifies the following content while examining the output of a debugger command over a client-server application: get connection (database01, "alpha " , "AXTV. 127GdCx94GTd") ;
Which of the following is the most likely vulnerability in this system?
- A . Lack of input validation
- B . SQL injection
- C . Hard-coded credential
- D . Buffer overflow attacks
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
- A . Review Of security requirements
- B . Compliance checks
- C . Decomposing the application
- D . Security by design
A security analyst needs to ensure that systems across the organization are protected based on the sensitivity of the content each system hosts. The analyst is working with the respective system owners to help determine the best methodology that seeks to promote confidentiality, availability,
and integrity of the data being hosted.
Which of the following should the security analyst perform first to
categorize and prioritize the respective systems?
- A . Interview the users who access these systems,
- B . Scan the systems to see which vulnerabilities currently exist.
- C . Configure alerts for vendor-specific zero-day exploits.
- D . Determine the asset value of each system.
Which of the following is the best reason to implement an MOU?
- A . To create a business process for configuration management
- B . To allow internal departments to understand security responsibilities
- C . To allow an expectation process to be defined for legacy systems
- D . To ensure that all metrics on service levels are properly reported
A security administrator has found indications of dictionary attacks against the company’s external-facing portal.
Which of the following should be implemented to best mitigate the password attacks?
- A . Multifactor authentication
- B . Password complexity
- C . Web application firewall
- D . Lockout policy
A company is concerned with finding sensitive file storage locations that are open to the public. The current internal cloud network is flat.
Which of the following is the best solution to secure the network?
- A . Implement segmentation with ACLs.
- B . Configure logging and monitoring to the SIEM.
- C . Deploy MFA to cloud storage locations.
- D . Roll out an IDS.
