CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
Which of the following can be used to learn more about TTPs used by cybercriminals?
- A . ZenMAP
- B . MITRE ATT&CK
- C . National Institute of Standards and Technology
- D . theHarvester
A security analyst is working on a server patch management policy that will allow the infrastructure team to be informed more quickly about new patches.
Which of the following would most likely be required by the infrastructure team so that vulnerabilities can be remediated quickly? (Select two).
- A . Hostname
- B . Missing KPI
- C . CVE details
- D . POC availability
- E . loCs
- F . npm identifier
A security analyst is reviewing the following log entries to identify anomalous activity:
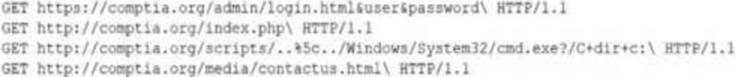
Which of the following attack types is occurring?
- A . Directory traversal
- B . SQL injection
- C . Buffer overflow
- D . Cross-site scripting
A security analyst performs a weekly vulnerability scan on a network that has 240 devices and receives a report with 2.450 pages.
Which of the following would most likely decrease the number of false positives?
- A . Manual validation
- B . Penetration testing
- C . A known-environment assessment
- D . Credentialed scanning
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system.
Which of the following steps of the process does this describe?
- A . Eradication
- B . Recovery
- C . Containment
- D . Preparation
Exploit code for a recently disclosed critical software vulnerability was publicly available (or download for several days before being removed.
Which of the following CVSS v.3.1 temporal metrics was most impacted by this exposure?
- A . Remediation level
- B . Exploit code maturity
- C . Report confidence
- D . Availability
Which of the following actions would an analyst most likely perform after an incident has been investigated?
- A . Risk assessment
- B . Root cause analysis
- C . Incident response plan
- D . Tabletop exercise
A Chief Information Security Officer wants to implement security by design, starting ……
vulnerabilities, including SQL injection, FRI, XSS, etc.
Which of the following would most likely meet the requirement?
- A . Reverse engineering
- B . Known environment testing
- C . Dynamic application security testing
- D . Code debugging
An organization receives a legal hold request from an attorney. The request pertains to emails related to a disputed vendor contract.
Which of the following is the first step for the security team to take to ensure compliance with the request?
- A . Publicly disclose the request to other vendors.
- B . Notify the departments involved to preserve potentially relevant information.
- C . Establish a chain of custody, starting with the attorney’s request.
- D . Back up the mailboxes on the server and provide the attorney with a copy.
Due to reports of unauthorized activity that was occurring on the internal network, an analyst is performing a network discovery. The analyst runs an Nmap scan against a corporate network to evaluate which devices were operating in the environment.
Given the following output:
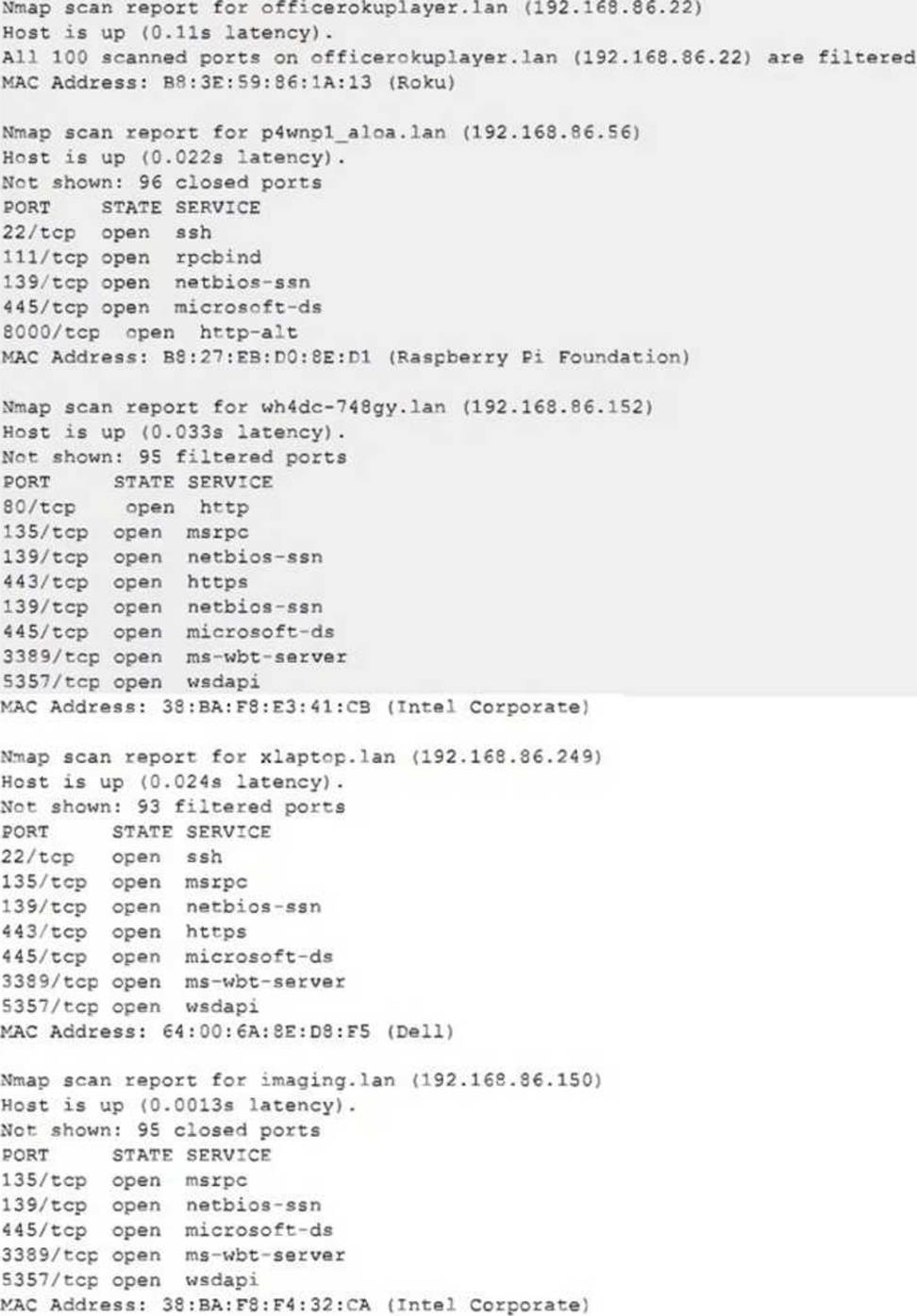
Which of the following choices should the analyst look at first?
- A . wh4dc-748gy.lan (192.168.86.152)
- B . lan (192.168.86.22)
- C . imaging.lan (192.168.86.150)
- D . xlaptop.lan (192.168.86.249)
- E . p4wnp1_aloa.lan (192.168.86.56)
