CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
Which Of the following techniques would be best to provide the necessary assurance for embedded software that drives centrifugal pumps at a power Plant?
- A . Containerization
- B . Manual code reviews
- C . Static and dynamic analysis
- D . Formal methods
Given the output below:
#nmap 7.70 scan initiated Tues, Feb 8 12:34:56 2022 as: nmap -v -Pn -p 80,8000,443 –script http-* -oA server.out 192.168.220.42
Which of the following is being performed?
- A . Cross-site scripting
- B . Local file inclusion attack
- C . Log4] check
- D . Web server enumeration
A systems administrator notices unfamiliar directory names on a production server. The administrator reviews the directory listings and files, and then concludes the server has been compromised.
Which of the following steps should the administrator take next?
- A . Inform the internal incident response team.
- B . Follow the company’s incident response plan.
- C . Review the lessons learned for the best approach.
- D . Determine when the access started.
An analyst is investigating a phishing incident and has retrieved the following as part of the investigation:
cmd.exe /c c:WindowsSystem32WindowsPowerShellv 1. 0powershell.exe -WindowStyle Hidden – ExecutionPolicy Bypass -NoLogo -NoProfile -EncodedCommand <VERY LONG STRING>
Which of the following should the analyst use to gather more information about the purpose of this command?
- A . Echo the command payload content into ‚base64 -d‘.
- B . Execute the command from a Windows VM.
- C . Use a command console with administrator privileges to execute the code.
- D . Run the command as an unprivileged user from the analyst workstation.
Which of the following responsibilities does the legal team have during an incident management event? (Select two).
- A . Coordinate additional or temporary staffing for recovery efforts.
- B . Review and approve new contracts acquired as a result of an event.
- C . Advise the Incident response team on matters related to regulatory reporting.
- D . Ensure all system security devices and procedures are in place.
- E . Conduct computer and network damage assessments for insurance.
- F . Verify that all security personnel have the appropriate clearances.
A forensic analyst is conducting an investigation on a compromised server
Which of the following should the analyst do first to preserve evidence“
- A . Restore damaged data from the backup media
- B . Create a system timeline
- C . Monitor user access to compromised systems
- D . Back up all log files and audit trails
A cryptocurrency service company is primarily concerned with ensuring the accuracy of the data on one of its systems. A security analyst has been tasked with prioritizing vulnerabilities for remediation for the system.
The analyst will use the following CVSSv3.1 impact metrics for prioritization:
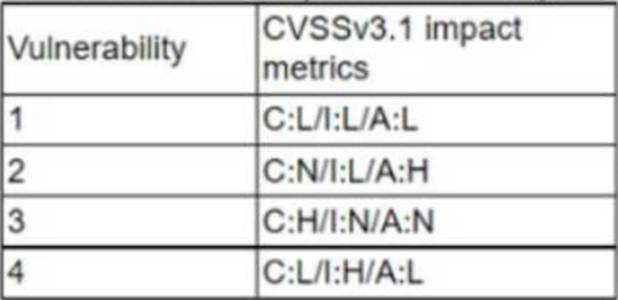
Which of the following vulnerabilities should be prioritized for remediation?
- A . 1
- B . 2
- C . 3
- D . 4
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
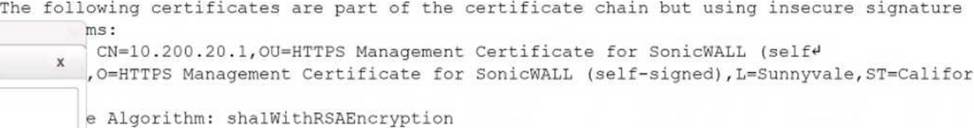
this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
- A . Reconfigure the device to support only connections leveraging TLSv1.2.
- B . Obtain a new self-signed certificate and select AES as the hashing algorithm.
- C . Replace the existing certificate with a certificate that uses only MD5 for signing.
- D . Use only signed certificates with cryptographically secure certificate sources.
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender.
Which of the following information security goals is the analyst most likely trying to achieve?
- A . Non-repudiation
- B . Authentication
- C . Authorization
- D . Integrity
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
- A . Mean time to detect
- B . Number of exploits by tactic
- C . Alert volume
- D . Quantity of intrusion attempts
