CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
A security analyst discovers an LFI vulnerability that can be exploited to extract credentials from the underlying host.
Which of the following patterns can the security analyst use to search the web server logs for evidence of exploitation of that particular vulnerability?
- A . /etc/ shadow
- B . curl localhost
- C . ; printenv
- D . cat /proc/self/
During an incident, a security analyst discovers a large amount of Pll has been emailed externally from an employee to a public email address. The analyst finds that the external email is the employee’s personal email.
Which of the following should the analyst recommend be done first?
- A . Place a legal hold on the employee’s mailbox.
- B . Enable filtering on the web proxy.
- C . Disable the public email access with CASB.
- D . Configure a deny rule on the firewall.
A security program was able to achieve a 30% improvement in MTTR by integrating security controls into a SIEM. The analyst no longer had to jump between tools.
Which of the following best describes what the security program did?
- A . Data enrichment
- B . Security control plane
- C . Threat feed combination
- D . Single pane of glass
HOTSPOT
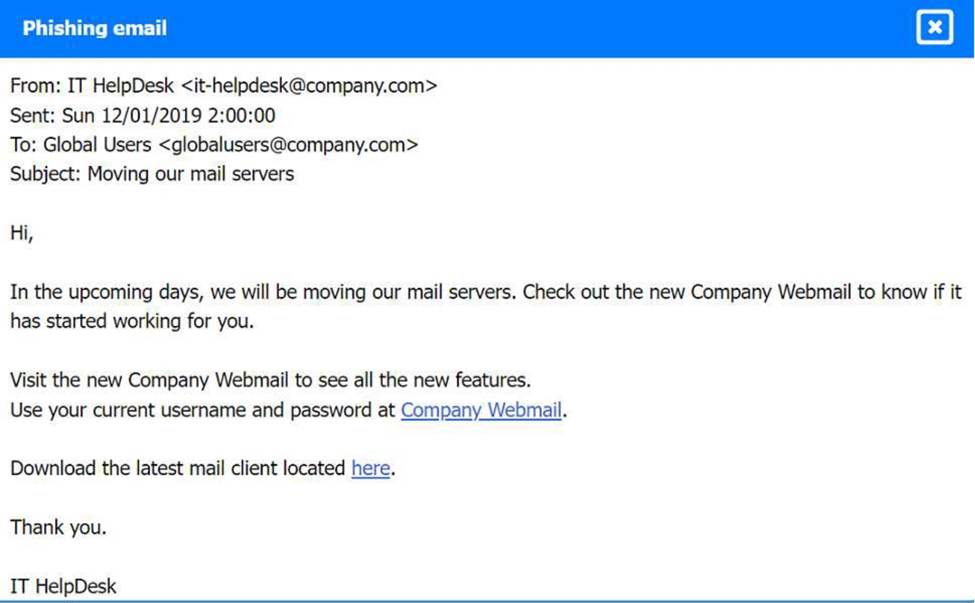
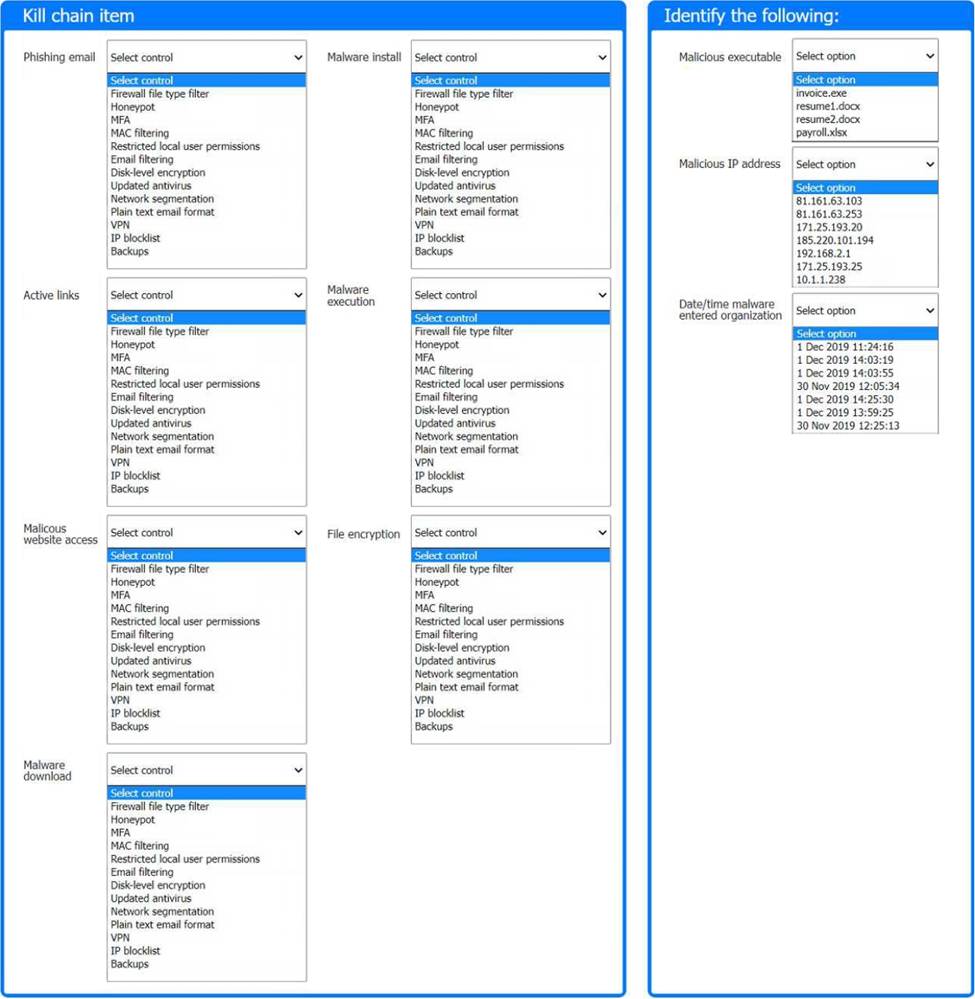
A company recently experienced a security incident. The security team has determined a user clicked on a link embedded in a phishing email that was sent to the entire company. The link resulted in a malware download, which was subsequently installed and run.
INSTRUCTIONS
Part 1
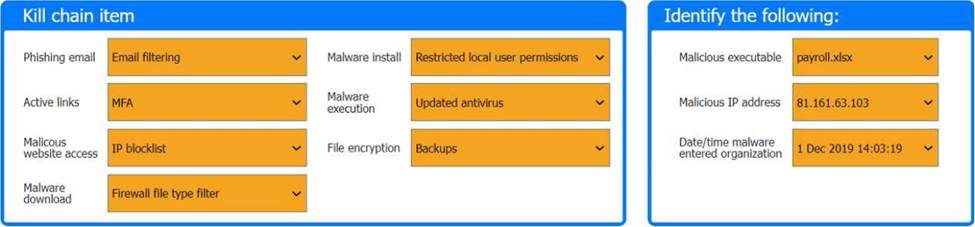
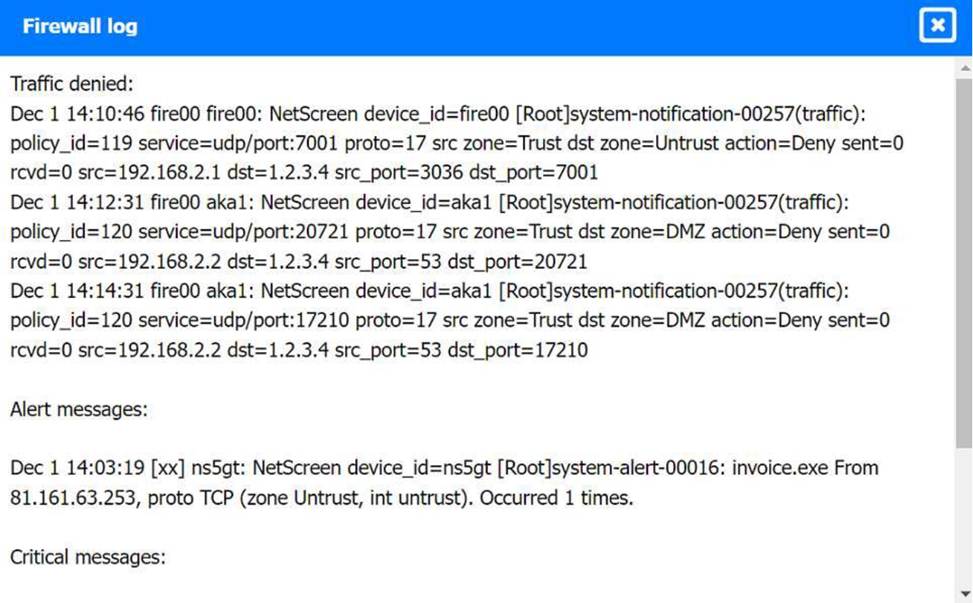
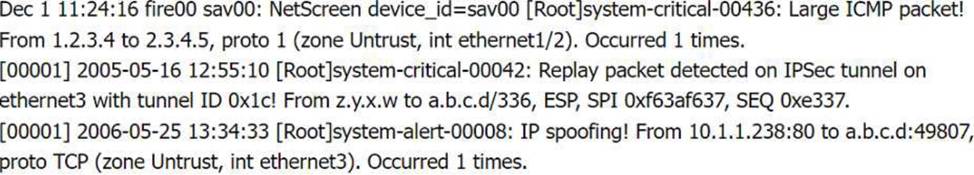
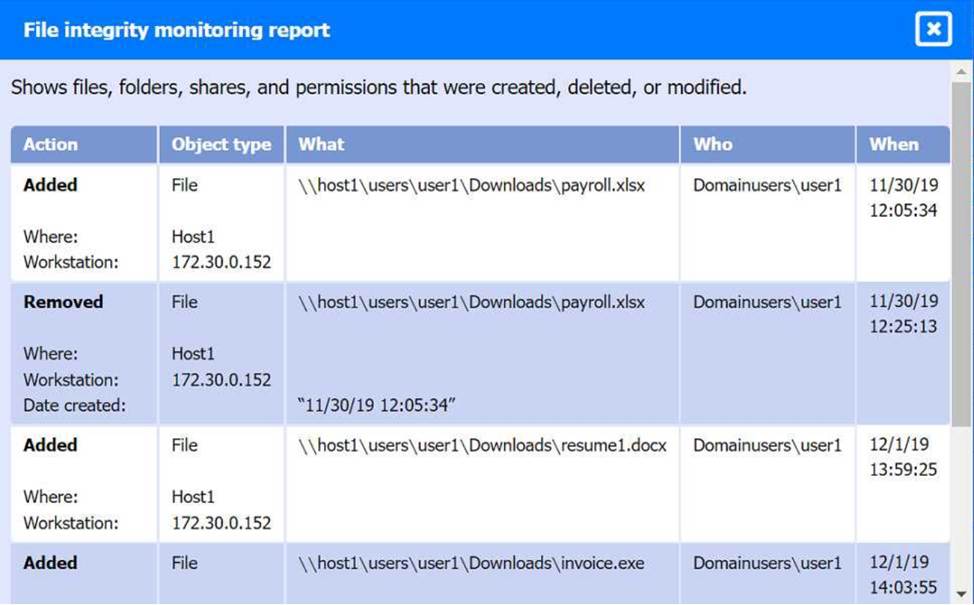
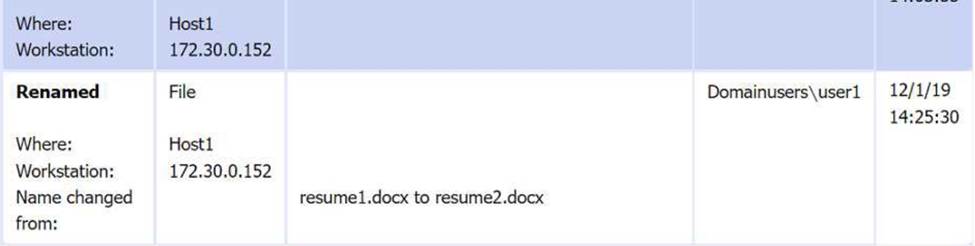
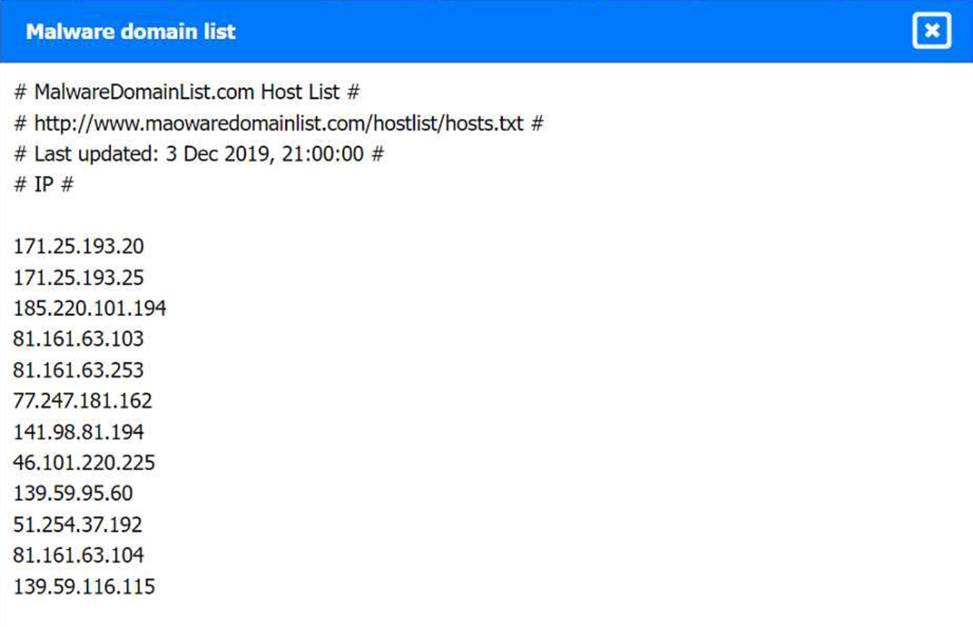
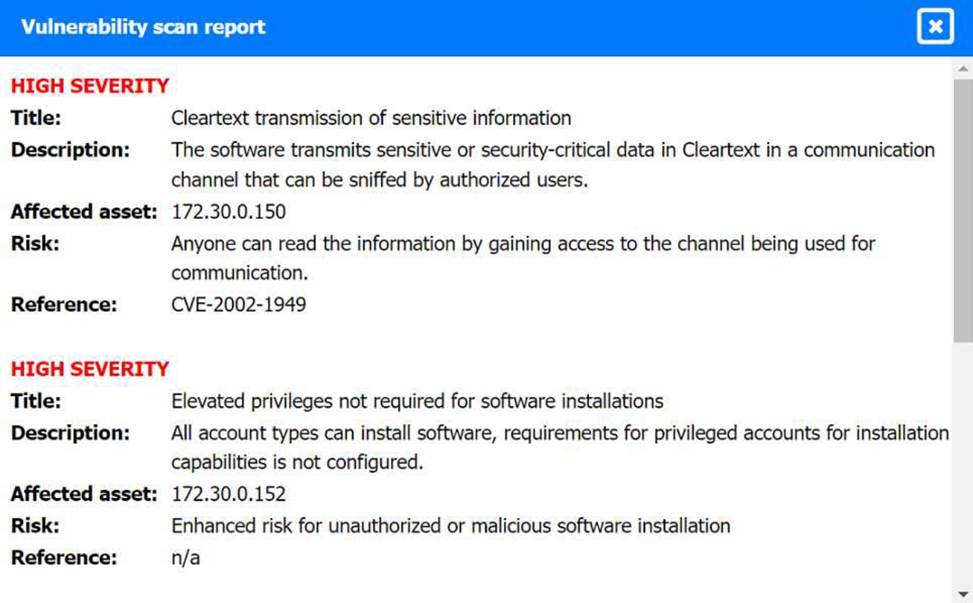
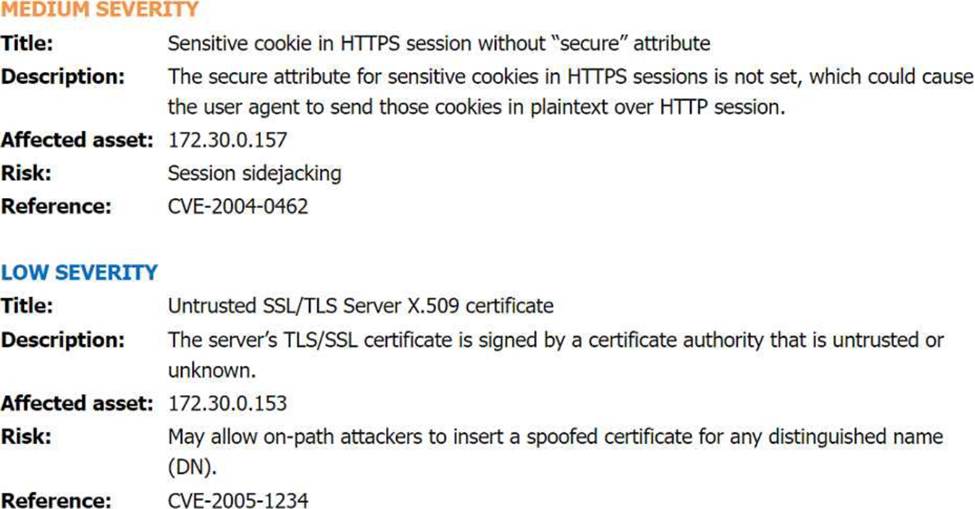
Review the artifacts associated with the security incident. Identify the name of the malware, the malicious IP address, and the date and time when the malware executable entered the organization.
Part 2
Review the kill chain items and select an appropriate control for each that would improve the security posture of the organization and would have helped to prevent this incident from occurring. Each control may only be used once, and not all controls will be used.

Firewall log:
File integrity Monitoring Report:
Malware domain list:
Vulnerability Scan Report:
Phishing Email:
A company creates digitally signed packages for its devices.
Which of the following best describes the
method by which the security packages are delivered to the company’s customers?
- A . Antitamper mechanism
- B . SELinux
- C . Trusted firmware updates
- D . eFuse
An incident response analyst is taking over an investigation from another analyst. The investigation has been going on for the past few days.
Which of the following steps is most important during the transition between the two analysts?
- A . Identify and discuss the lessons learned with the prior analyst.
- B . Accept all findings and continue to investigate the next item target.
- C . Review the steps that the previous analyst followed.
- D . Validate the root cause from the prior analyst.
Which of the following best explains the importance of communicating with staff regarding the official public communication plan related to incidents impacting the organization?
- A . To establish what information is allowed to be released by designated employees
- B . To designate an external public relations firm to represent the organization
- C . To ensure that all news media outlets are informed at the same time
- D . To define how each employee will be contacted after an event occurs
Which of the following would eliminate the need for different passwords for a variety or internal application?
- A . CASB
- B . SSO
- C . PAM
- D . MFA
A security analyst is logged on to a jump server to audit the system configuration and status.
The organization’s policies for access to and configuration of the jump server include the following:
• No network access is allowed to the internet.
• SSH is only for management of the server.
• Users must utilize their own accounts, with no direct login as an administrator.
• Unnecessary services must be disabled.
The analyst runs netstar with elevated permissions and receives the following output:
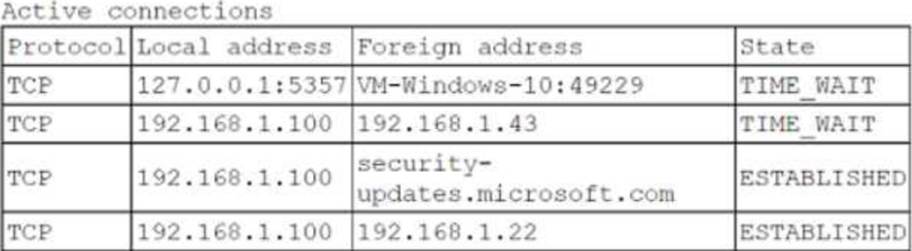
Which of the following policies does the server violate?
- A . Unnecessary services must be disabled.
- B . SSH is only for management of the server.
- C . No network access is allowed to the internet.
- D . Users must utilize their own accounts, with no direct login as an administrator.
Which of the following is a useful tool for mapping, tracking, and mitigating identified threats and vulnerabilities with the likelihood and impact of occurrence?
- A . Risk register
- B . Vulnerability assessment
- C . Penetration test
- D . Compliance report