CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
Which of the following in the digital forensics process is considered a critical activity that often includes a graphical representation of process and operating system events?
- A . Registry editing
- B . Network mapping
- C . Timeline analysis
- D . Write blocking
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company:
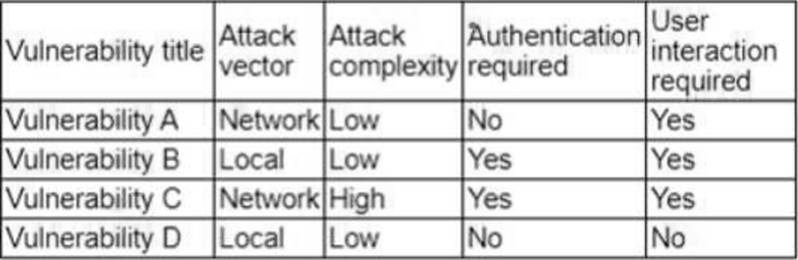
Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
- A . Vulnerability A
- B . Vulnerability B
- C . Vulnerability C
- D . Vulnerability D
After a security assessment was done by a third-party consulting firm, the cybersecurity program recommended integrating DLP and CASB to reduce analyst alert fatigue.
Which of the following is the best possible outcome that this effort hopes to achieve?
- A . SIEM ingestion logs are reduced by 20%.
- B . Phishing alerts drop by 20%.
- C . False positive rates drop to 20%.
- D . The MTTR decreases by 20%.
A company has the following security requirements:
. No public IPs
・ All data secured at rest
. No insecure ports/protocols
After a cloud scan is completed, a security analyst receives reports that several misconfigurations are putting the company at risk.
Given the following cloud scanner output:
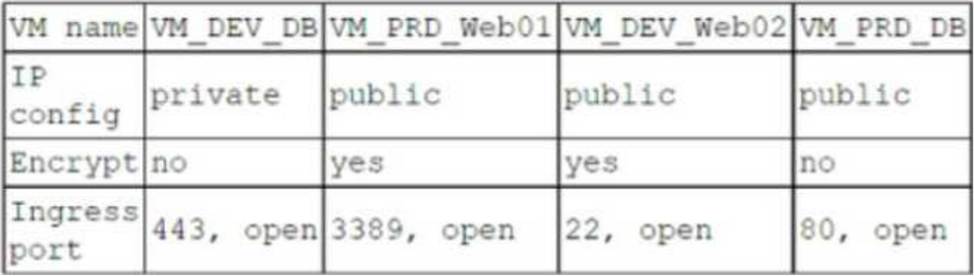
Which of the following should the analyst recommend be updated first to meet the security requirements and reduce risks?
- A . VM_PRD_DB
- B . VM_DEV_DB
- C . VM_DEV_Web02
- D . VM_PRD_Web01
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident.
Based on the following host list:
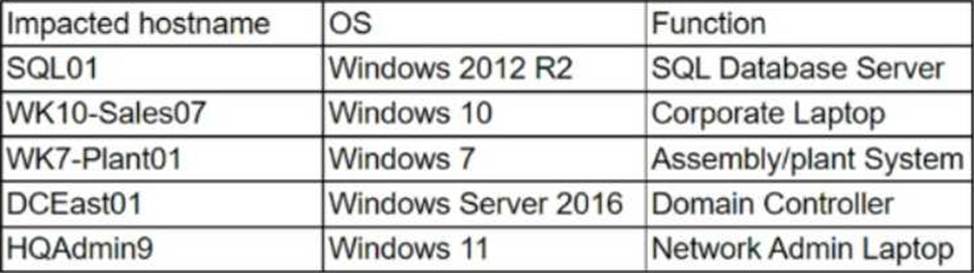
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
- A . SQL01
- B . WK10-Sales07
- C . WK7-Plant01
- D . DCEast01
- E . HQAdmin9
A security analyst discovers the accounting department is hosting an accounts receivable form on a public document service. Anyone with the link can access it.
Which of the following threats applies to this situation?
- A . Potential data loss to external users
- B . Loss of public/private key management
- C . Cloud-based authentication attack
- D . Identification and authentication failures
Due to an incident involving company devices, an incident responder needs to take a mobile phone to the lab for further investigation.
Which of the following tools should be used to maintain the integrity of the mobile phone while it is transported? (Select two).
- A . Signal-shielded bag
- B . Tamper-evident seal
- C . Thumb drive
- D . Crime scene tape
- E . Write blocker
- F . Drive duplicator
A security analyst who works in the SOC receives a new requirement to monitor for indicators of
compromise.
Which of the following is the first action the analyst should take in this situation?
- A . Develop a dashboard to track the indicators of compromise.
- B . Develop a query to search for the indicators of compromise.
- C . Develop a new signature to alert on the indicators of compromise.
- D . Develop a new signature to block the indicators of compromise.
New employees in an organization have been consistently plugging in personal webcams despite the company policy prohibiting use of personal devices. The SOC manager discovers that new employees are not aware of the company policy.
Which of the following will the SOC manager most likely recommend to help ensure new employees are accountable for following the company policy?
- A . Human resources must email a copy of a user agreement to all new employees
- B . Supervisors must get verbal confirmation from new employees indicating they have read the user agreement
- C . All new employees must take a test about the company security policy during the cjitoardmg process
- D . All new employees must sign a user agreement to acknowledge the company security policy
A report contains IoC and TTP information for a zero-day exploit that leverages vulnerabilities in a specific version of a web application.
Which of the following actions should a SOC analyst take first after receiving the report?
- A . Implement a vulnerability scan to determine whether the environment is at risk.
- B . Block the IP addresses and domains from the report in the web proxy and firewalls.
- C . Verify whether the information is relevant to the organization.
- D . Analyze the web application logs to identify any suspicious or malicious activity.
