CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 02.02.2026
An end-of-life date was announced for a widely used OS. A business-critical function is performed by some machinery that is controlled by a PC, which is utilizing the OS that is approaching the end-of-life date.
Which of the following best describes a security analyst’s concern?
- A . Any discovered vulnerabilities will not be remediated.
- B . An outage of machinery would cost the organization money.
- C . Support will not be available for the critical machinery
- D . There are no compensating controls in place for the OS.
Which of the following most accurately describes the Cyber Kill Chain methodology?
- A . It is used to correlate events to ascertain the TTPs of an attacker.
- B . It is used to ascertain lateral movements of an attacker, enabling the process to be stopped.
- C . It provides a clear model of how an attacker generally operates during an intrusion and the actions to take at each stage
- D . It outlines a clear path for determining the relationships between the attacker, the technology used, and the target
Which of the following is a nation-state actor least likely to be concerned with?
- A . Detection by MITRE ATT&CK framework.
- B . Detection or prevention of reconnaissance activities.
- C . Examination of its actions and objectives.
- D . Forensic analysis for legal action of the actions taken
An analyst is reviewing a dashboard from the company’s SIEM and finds that an IP address known to be malicious can be tracked to numerous high-priority events in the last two hours. The dashboard indicates that these events relate to TTPs.
Which of the following is the analyst most likely using?
- A . MITRE ATT&CK
- B . OSSTMM
- C . Diamond Model of Intrusion Analysis
- D . OWASP
While performing a dynamic analysis of a malicious file, a security analyst notices the memory address changes every time the process runs.
Which of the following controls is most likely preventing the analyst from finding the proper memory address of the piece of malicious code?
- A . Address space layout randomization
- B . Data execution prevention
- C . Stack canary
- D . Code obfuscation
A security analyst observed the following activity from a privileged account:
. Accessing emails and sensitive information
. Audit logs being modified
. Abnormal log-in times
Which of the following best describes the observed activity?
- A . Irregular peer-to-peer communication
- B . Unauthorized privileges
- C . Rogue devices on the network
- D . Insider attack
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero trust approach. The IT security team is required to come up with priorities for the program.
Which of the following is the best priority based on common attack frameworks?
- A . Reduce the administrator and privileged access accounts
- B . Employ a network-based IDS
- C . Conduct thorough incident response
- D . Enable SSO to enterprise applications
The following output is from a tcpdump al the edge of the corporate network:
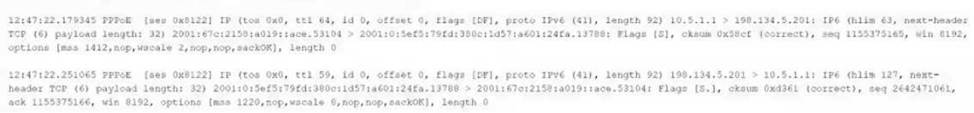
Which of the following best describes the potential security concern?
- A . Payload lengths may be used to overflow buffers enabling code execution.
- B . Encapsulated traffic may evade security monitoring and defenses
- C . This traffic exhibits a reconnaissance technique to create network footprints.
- D . The content of the traffic payload may permit VLAN hopping.
The following output is from a tcpdump al the edge of the corporate network:

Which of the following best describes the potential security concern?
- A . Payload lengths may be used to overflow buffers enabling code execution.
- B . Encapsulated traffic may evade security monitoring and defenses
- C . This traffic exhibits a reconnaissance technique to create network footprints.
- D . The content of the traffic payload may permit VLAN hopping.
The security team reviews a web server for XSS and runs the following Nmap scan:

Which of the following most accurately describes the result of the scan?
- A . An output of characters > and " as the parameters used m the attempt
- B . The vulnerable parameter ID hccp://l72.31.15.2/1.php?id-2 and unfiltered characters returned
- C . The vulnerable parameter and unfiltered or encoded characters passed > and " as unsafe
- D . The vulnerable parameter and characters > and " with a reflected XSS attempt
