DELL EMC D-ISM-FN-23 Übungsprüfungen
Zuletzt aktualisiert am 31.08.2025- Prüfungscode: D-ISM-FN-23
- Prüfungsname: Dell Information Storage and Management Foundations 2023
- Zertifizierungsanbieter: DELL EMC
- Zuletzt aktualisiert am: 31.08.2025
In a data archiving environment, which component scans primary storage to find the files that are required to archive?
- A . Archive stub file
- B . Archive agent
- C . Archive storage
- D . Archive database server
An application uses ten, 15 GB devices. A pointer-based full volume replica of the application is required. The replica will be kept for 24 hours and the data changes by 10% every 24 hours.
How much storage should be allocated for the replication?
- A . 15 GB
- B . 30 GB
- C . 150 GB
- D . 300 GB
What does the transformation of an operating model for third platform adoption involve?
- A . Provisioning IT resources through a self-service portal
- B . Establishing new roles and responsibilities to manage IT services
- C . Adopting virtualization technologies to enable automation
- D . Building new technical and business skills in the IT staff
What is a specialized replication technique that enables moving data from one storage system to another within a data center without incurring downtime?
- A . VM-level backup
- B . Archive
- C . Migration
- D . Image-level backup
Which data protection solution provides the ability to select a backup technology based on demand?
- A . Agent-Based backup
- B . Cloud-Based backup
- C . File-Based backup
- D . Image-Based backup
Which network performance attribute is achieved when using flow control in FOP?
- A . In-order packet delivery
- B . IP network congestion detection and handling
- C . Eliminate IP packet fragmentation
- D . IP packet collision detection and handling
What determines how far back the recovery points can go in a continuous data protection (CDP) solution?
- A . Amount of space that is configured for the journal
- B . Size of the CDP appliance used for replication
- C . Size of the source and replica volumes
- D . Type of write splitter used for replication
Which elements are associated with an object in an object-based storage system?
- A . Data, metadata, object ID, and attributes
- B . LUN ID, data, metadata, and object ID
- C . Metadata, object ID, attributes, and file path
- D . Object ID, attributes, LUN ID, and file path
Which global addressing does the REST application programming interface use for the discovery of a storage service?
- A . Uniform Resource Identifier
- B . Namespace
- C . Extensible Markup Language
- D . Controller-provided MAC address
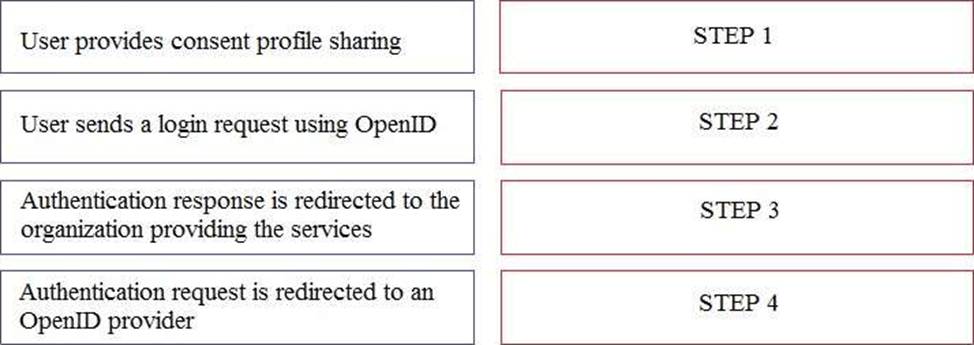
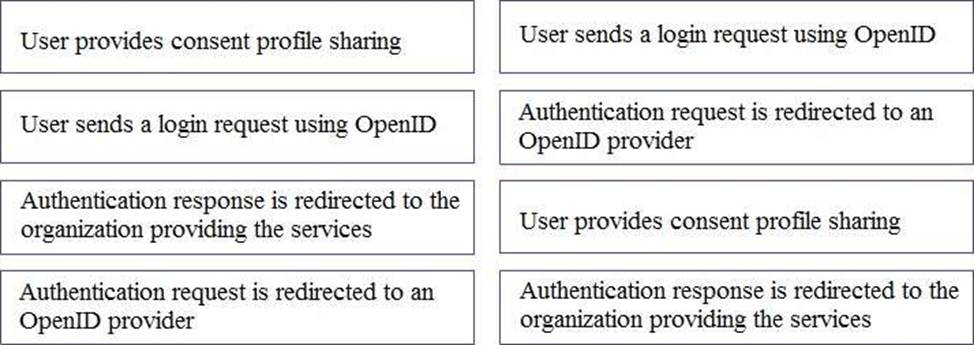
To authenticate a user using OpenID authentication control, what are the correct sequence of steps?