DELL EMC D-ISM-FN-23 Übungsprüfungen
Zuletzt aktualisiert am 03.09.2025- Prüfungscode: D-ISM-FN-23
- Prüfungsname: Dell Information Storage and Management Foundations 2023
- Zertifizierungsanbieter: DELL EMC
- Zuletzt aktualisiert am: 03.09.2025
In the context of storage security, what is the primary goal of data encryption?
- A . To speed up data access
- B . To protect data confidentiality
- C . To ensure data deduplication
- D . To manage user access
Which layer of the OSI reference model is responsible for logical addressing and routing?
- A . Data Link
- B . Session
- C . Network
- D . Transport
What is an accurate statement about a denial-of-service attack?
- A . Prevents legitimate users from accessing resources or services
- B . Intentional misuse of privileges to compromise data security
- C . Gaining unauthorized access to a user’s accounts and data
- D . Captures a user’s credentials and then sends to the attacker
Which operation is represented in the exhibit?
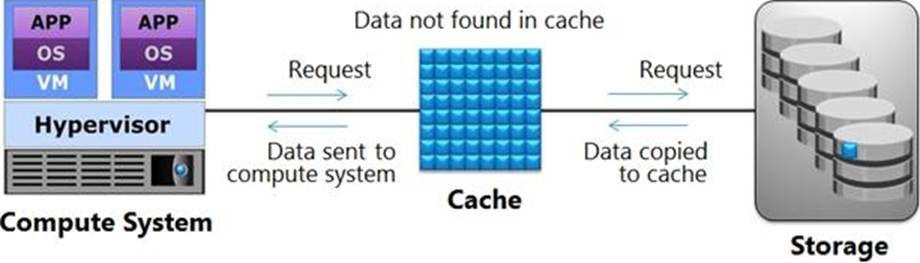
- A . Write-back Cache
- B . Read Cache Miss
- C . Write-through Cache
- D . Read Cache Hit
What is an accurate statement about a hybrid cloud?
- A . Supports data and application portability for load balancing between clouds
- B . Allows organizations with common concerns to share the cost of deploying the cloud
- C . Enables the entire cloud infrastructure to be controlled by the consumer’s IT staff
- D . Allows an organization to outsource the implementation of a private cloud to a cloud provider
How is NVMe used to connect a host to M.2 storage devices?
- A . through an embedded PCIe controller
- B . through a PCIe bus FC HBA card
- C . through a PCIe bus card
- D . through an embedded FC HBA controller
Which type of login is performed between an N_Port and an F_Port in a Fibre Channel SAN environment?
- A . FLOGI
- B . PLOGI
- C . PRLI
- D . WWPN
A company’s assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
- A . Minimize the work factor
- B . Easy access to assets by authorized users
- C . Limited access to assets by unauthorized users
- D . Maximize the attack surface
What role does an Intrusion Detection System (IDS) play in protecting a storage infrastructure?
- A . Encrypts data at rest
- B . Monitors network traffic for suspicious activity
- C . Provides physical security to storage devices
- D . Manages user access rights
What is a benefit of backing up data to a disk library?
- A . Provides improved backup and recovery performance
- B . Provides built-in portability to meet offsite requirements
- C . Supports the shoe shining effect for improved backup performance
- D . Pre-configured and dedicated appliance is only used for backups
