DELL EMC D-ISM-FN-23 Übungsprüfungen
Zuletzt aktualisiert am 28.08.2025- Prüfungscode: D-ISM-FN-23
- Prüfungsname: Dell Information Storage and Management Foundations 2023
- Zertifizierungsanbieter: DELL EMC
- Zuletzt aktualisiert am: 28.08.2025
What is a key advantage of implementing FCIP?
- A . Provides a disaster recovery solution by replicating data across data centers.
- B . Enables migration of VMs across data centers by using existing FC networks.
- C . Ensures lossless transmission of FC traffic across data centers over Ethernet.
- D . Provides a dedicated network for transmission of storage traffic within a data center.
Which operation is performed by a scale-out NAS cluster when clients send data to the cluster?
- A . Data is divided and stored on multiple nodes in parallel
- B . Data is consolidated into a block and then stored on the NAS head
- C . Data is evenly distributed to every file system in the cluster
- D . NAS file system and cluster grow dynamically to store the data
Refer to the exhibit.
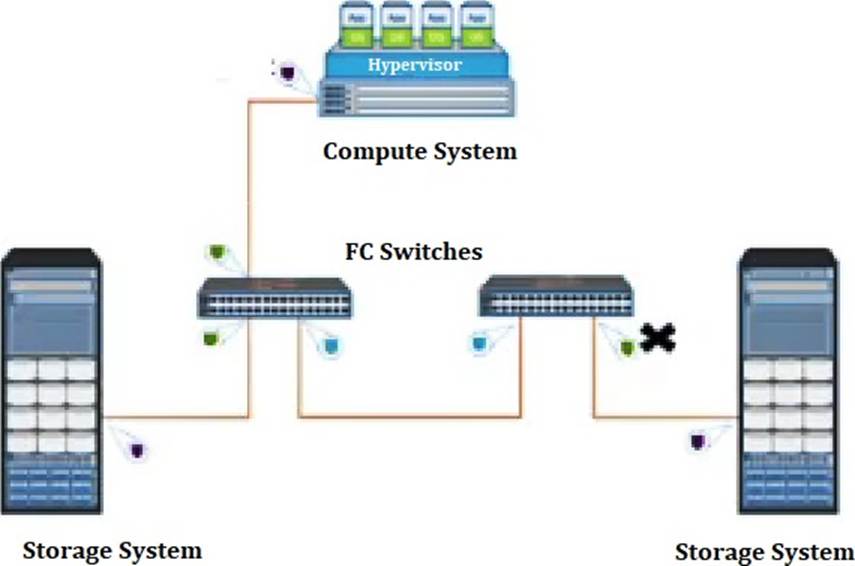
What type of Fibre Channel port does the “X” represent?
- A . N_port
- B . F_port
- C . E_port
- D . NL_port
A company needs to transmit data over long distances between their disparate FC SANs at multiple geographic locations.
Which recommended protocol should be adopted by the company?
- A . iSCSI
- B . FCIP
- C . FC
- D . FCoE
Which security control allows a client to access protected resources from a resource server on behalf of a resource owner?
- A . Zoning
- B . OAuth
- C . OpenID
- D . LUN Masking
Which type of interface connects SSD drives to the storage array controller?
- A . NVMe/IB
- B . NVMe/TCP
- C . NVMe
- D . NVMe-oF
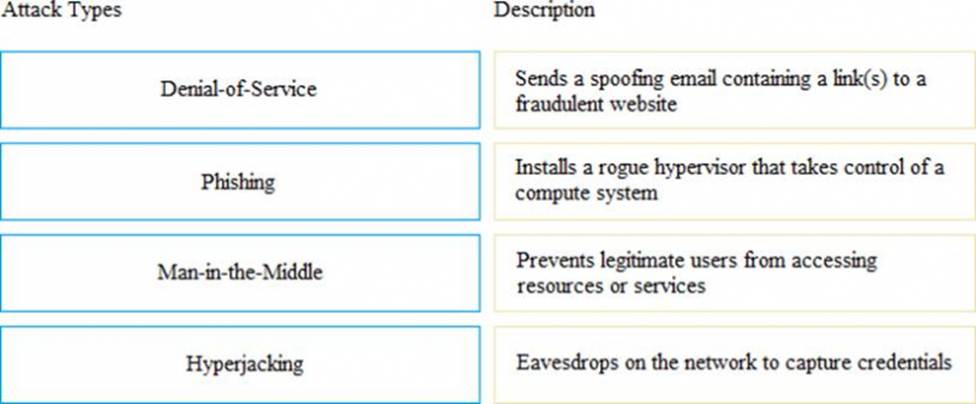
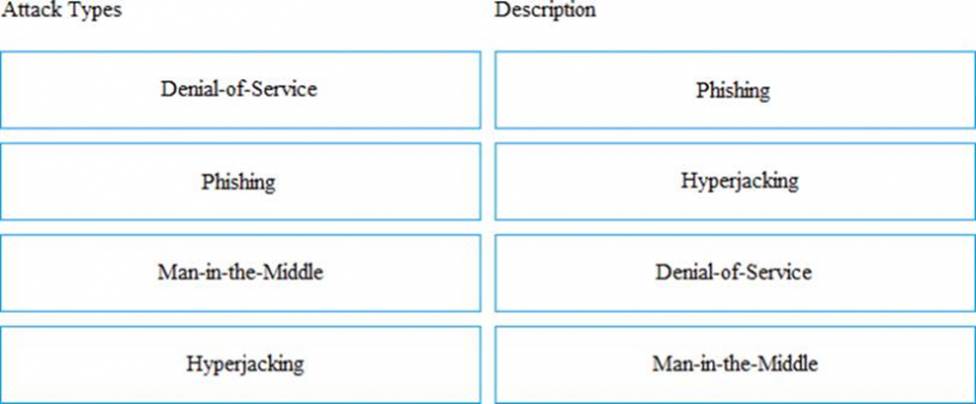
What is an impact of a Denial-of-Service attack?
- A . Privileges are intentionally misused to compromise data security
- B . User’s credentials are eavesdropped by the attacker
- C . Computing resources are exhausted and made unavailable to users
- D . User’s accounts and data are compromised by malicious insiders
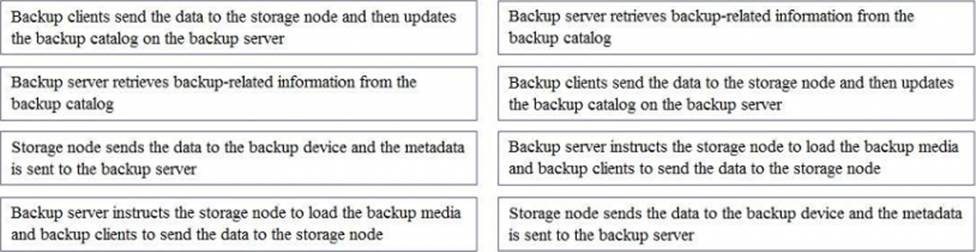
In a backup operation, what are the correct sequence of steps after the backup server initiates the scheduled backup process?