Fortinet FCSS_ADA_AR-6.7 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: FCSS_ADA_AR-6.7
- Prüfungsname: FCSS—Advanced Analytics 6.7 Architect
- Zertifizierungsanbieter: Fortinet
- Zuletzt aktualisiert am: 02.02.2026
What happens to UEBA events when a user is off-net?
- A . The agent will upload the events to the Worker if it cannot upload them to a FortiSIEM collector
- B . The agent will cache events locally if it cannot upload them to a FortiSIEM collector
- C . The agent will upload the events to the Supervisor if it cannot upload them to a FortiSIEM collector
- D . The agent will drop the events if it cannot upload them to a FortiSIEM collector
Which of the following is crucial when defining and deploying collectors and agents in a SOC environment?
- A . Ensuring high-speed internet connectivity.
- B . Managing software licenses effectively.
- C . Ensuring compatibility with the target system.
- D . Coordinating with the software vendor for updates.
The main benefit of a multi-tenancy SOC solution for an MSSP is:
- A . Decreased overhead costs.
- B . The ability to host multiple tenants within a shared environment.
- C . Increased storage capacity for logs.
- D . Automatic software updates across all agents.
A service provider purchased a licensed EPS of 520 and the total unused events is 72,000. Calculate the total amount of allowed events for the next 3-minute interval.
- A . 192,456
- B . 192,442
- C . 192,446
- D . 192,450
How do customers connect to a shared multi-tenant instance on FortiSOAR?
- A . The MSSP must provide secure network connectivity between the FortiSOAR manager node and the customer devices.
- B . The MSSP must install a Secure Message Exchange node to connect to the customer’s shared multi-tenant instance.
- C . The customer must install a tenant node to connect to the MSSP shared multi-tenant instance.
- D . The MSSP must install an agent node on the customer’s network to connect to the customer’s shared multi-tenant instance.
Refer to the exhibit.
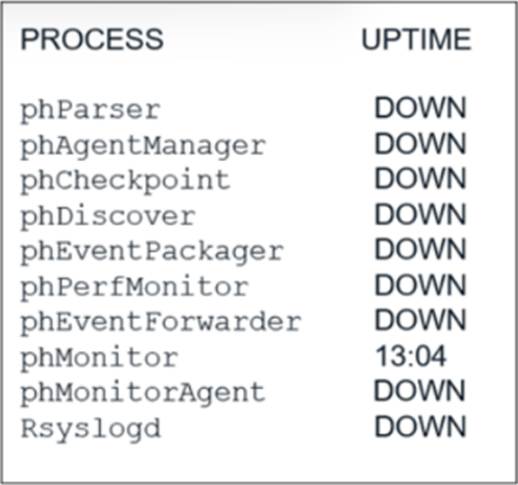
An administrator deploys a new collector for the first time, and notices that all the processes except the phMonitor are down.
How can the administrator bring the processes up?
- A . The administrator needs to run the command phtools –start all on the collector.
- B . Rebooting the collector will bring up the processes.
- C . The processes will come up after the collector is registered to the supervisor.
- D . The collector was not deployed properly and must be redeployed.
Which of the following is a primary reason to deploy FortiSIEM agents on both Windows and Linux platforms?
- A . To cover a diverse range of operating systems in an environment.
- B . To increase the speed of the SOC server.
- C . To provide redundancy in case one platform fails.
- D . To prevent users from installing unauthorized software.
What are the benefits of understanding the MITRE ATT&CK® framework in the context of FortiSIEM?
- A . Enhancing rule creation based on known attack patterns?
- B . Streamlining software updates for FortiSIEM?
- C . Improving the correlation of security events?
- D . Implementing effective response strategies to detected threats?
When integrating FortiSOAR with FortiSIEM for remediation, the primary goal is to:
- A . Reduce the need for human intervention during incidents?
- B . Create visual graphs for board meetings?
- C . Archive older incidents for record-keeping?
- D . Add new features to the FortiSIEM dashboard?
If an unusual spike in network traffic is detected, which tool would be most effective in automating a response action?
- A . FortiSOAR?
- B . FortiAntivirus?
- C . FortiStorage?
- D . FortiUser?
