Huawei H12-891_V1.0-ENU Übungsprüfungen
Zuletzt aktualisiert am 21.10.2025- Prüfungscode: H12-891_V1.0-ENU
- Prüfungsname: HCIE-Datacom V1.0
- Zertifizierungsanbieter: Huawei
- Zuletzt aktualisiert am: 21.10.2025
When the network administrator tried to access the internal network device through Telnet, he found that he could not access it. Which of the following reasons is impossible?
- A . The route is unreachable and the client and server cannot establish a TCP connection.
- B . ACL is bound in the VTY user interface
- C . Protocol inbound all is configured in the VTY user interface.
- D . The number of users logged into the device has reached the upper limit.
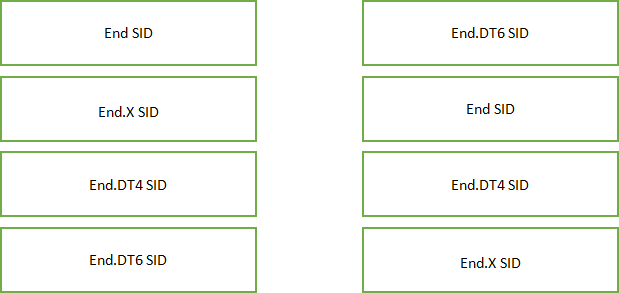
There are many types of SRv6 SIDs, and different types of SRv6 SIDs represent different functions. Please match the SRv6 SID type with its functionality.

When configuring access authentication, you need to define various contents authorized to the user in the authorization result. Which of the following does not include?
- A . Security group
- B . IP address
- C . VLAN
- D . ACL
As shown in the figure, 802.1X authentication is deployed on GE0/0/1 of Sw2. Which items in the following description are correct? (Multiple choice)

- A . When using interface-based access control, assuming that 802.1X client A is successfully authenticated, 802.1X client B can use network resources without authentication.
- B . Assume that SW2 adopts interface-based access control and 802.1X client A passes the authentication first. If 802.1N client A goes offline first, 802.1x client B will lose the corresponding network access rights.
- C . When using the MAC address-based access control method, both 802.1.x authentication client A and 802.1X authentication client B need to be authenticated separately to obtain the corresponding network access rights.
- D . Assume that SW2 adopts the MAC-based access control method and 802.1N client A passes the authentication first. If 802.1x client A goes offline first, since the port status does not change, 802.1X client B will Continue to retain appropriate network access rights
YANG is the data modeling language of NETCONF. Which of the following items belong to the YANG basic data model? (Multiple choice)
- A . Leaf node
- B . Tree node
- C . Set node
- D . List node
The network administrator wants to use the IP Prefix List to match specific routing entries. Which of the following routing entries will be matched by the IP Prefix List in the figure? (Multiple choice)
![]()
- A . 10.0.1.0/24
- B . 10.0.0.1/30
- C . 10.0.2.0/24
- D . 10.0.0.0/24
In the scenario of dynamically establishing a VXLAN tunnel through BGP EVPN, which of the following descriptions about the role of BGP EVPN Type5 routing is wrong?
- A . Type5 routing can carry the host IP address. At this time, it has the same function as IRB type routing. It is mainly used for host IP route advertisement in distributed gateway scenarios.
- B . Type5 routing will carry L3 VNI
- C . Type5 routing will carry L2 VNI
- D . Type5 routing carries routing information through the IP Prefix Length and IP Prefix fields.
BGP authentication can prevent illegal routers from establishing neighbors with BGP routers. BGP authentication can be divided into MD5 authentication and Keychain authentication. Which of the following packets will carry BGP Keychain authentication information? (Multiple choice)
- A . Notification
- B . Open
- C . Update
- D . Keepalive
According to different implementation levels, wide area VPN can be divided into L2VPN and L3VPN. Which of the following descriptions of wide-area VPNs is wrong?
- A . Traditional L3VPN uses VPN instances to isolate services and uses BGP VPNv4/v6 to transmit routes.
- B . EVPN supports L2VPN and L3VPN control plane
- C . On Huawei equipment, EVPN uses different address families for L2VPN and L3VPN services.
- D . Traditional L2VPN mainly includes VPLS and VWS, and virtual links can be established using LDP or BGP.
Which of the following descriptions about labels is wrong?
- A . The LSP established by statically assigning labels can also be dynamically adjusted according to network topology changes without administrator intervention.
- B . The principle to be followed when manually assigning labels is that the value of the outgoing label of the upstream node is the value of the incoming label of the downstream node.
- C . LSP is divided into two types: static LSP and dynamic LS: Static LP is manually configured by the administrator, and dynamic LSP is dynamically established using label protocol.
- D . Dynamic SP is dynamically established through label publishing protocols, such as MP-BGP, RSVP-TE, and LDP