Huawei H12-891_V1.0-ENU Übungsprüfungen
Zuletzt aktualisiert am 19.10.2025- Prüfungscode: H12-891_V1.0-ENU
- Prüfungsname: HCIE-Datacom V1.0
- Zertifizierungsanbieter: Huawei
- Zuletzt aktualisiert am: 19.10.2025
Assume that the neighbor relationship between BGP routers has been successfully established, and the configuration on R1 is as shown in the figure.
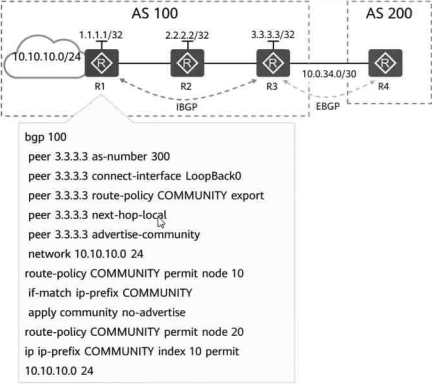
Then to which router can the routing entry 10.10.10.0/24 published by R1 be transmitted farthest?
- A . R4
- B . R1
- C . R2
- D . R3
When troubleshooting the EBGP neighbor relationship, the network administrator found that two directly connected devices used Loopback ports to establish connections, so they ran display current-configuration configuration bgp to view the configuration of peer ebgp max-hop hop-count.
Which of the following descriptions of this command is correct?
- A . hop-count must be greater than 1
- B . hop-count must be greater than 255
- C . hop-count must be greater than 2
- D . hop-count must be greater than 15
When a terminal device accesses a campus network where MAC bypass authentication is deployed, the access device will first perform MAC authentication on the terminal device. If authentication fails three times in a row, the terminal device needs to actively initiate 802.1X authentication.
- A . True
- B . False
All routers in a network enable SR-MPLS, and R1 encapsulates the label information of a data packet as shown in the figure. Which of the following is the forwarding path of the data packet at this time?
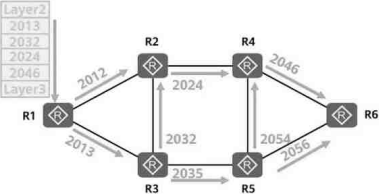
- A . R1-R2-R4-R6
- B . R1-R3-R5-R6
- C . R1-R3-R2-R4-R6
- D . R1-R2-R2-R5-R6
IPsec SA (Security Association, Security Association) has two generation methods, namely manual method and IKE automatic negotiation method.
Which of the following descriptions of these two methods is wrong?
- A . Both manual and IKE-established SAs support dynamic refresh.
- B . The lifetime of an SA established in IKE mode is controlled by the lifetime parameters configured by both parties.
- C . In manual mode, all parameters required to establish SA, including encryption/verification keys, etc., need to be manually configured by the user.
- D . In IKE mode, the encryption/verification key required to establish SA is generated through the DH algorithm.
Which of the following information can be included in the DHCP binding table? (Multiple choice)
- A . Lease time
- B . Ports and UDP ports
- C . MAC address
- D . IP address
Which of the following methods are used to establish IPsec SA? (Multiple choice)
- A . Manual creation
- B . Creation of certificate negotiation method
- C . Template negotiation method establishment
- D . IKE mode establishment
The NETCONF protocol provides a set of mechanisms for managing network devices. The operation object of NETCONF is the configuration library of the network device. Which of the following descriptions of the configuration library is wrong?
- A . <commit> will submit the configuration in the startup configuration library to become the configuration in the running configuration library
- B . The configuration library of network equipment can be divided into candidate configuration library, running configuration library and startup configuration library
- C . <validate> is an operation on the candidate configuration library
- D . <delete-config> is an operation on the startup configuration library
All routers in a network enable the SR-MPLS function based on OSPF. By default, when R3 forwards a packet with the destination address 10.0.4.4, its MPLS label is as shown in the figure.
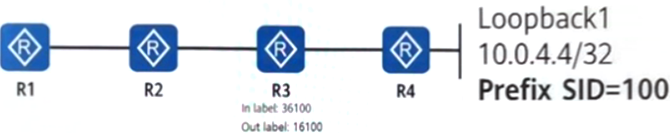
Then the SRCB range of R3 may be which of the following?
- A . 36000-65535
- B . 100-65535
- C . 16100-36100
- D . 16000-65530
Which of the following descriptions of LDP free label retention methods are correct? (Multiple choice)
- A . Save memory and label space
- B . Requires more memory and label space
- C . Keep all labels distributed by neighbors
- D . Only keep labels from next-hop neighbors and discard all labels from non-next-hop neighbors.
