Microsoft AZ-500 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: AZ-500
- Prüfungsname: Microsoft Azure Security Technologies
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 02.02.2026
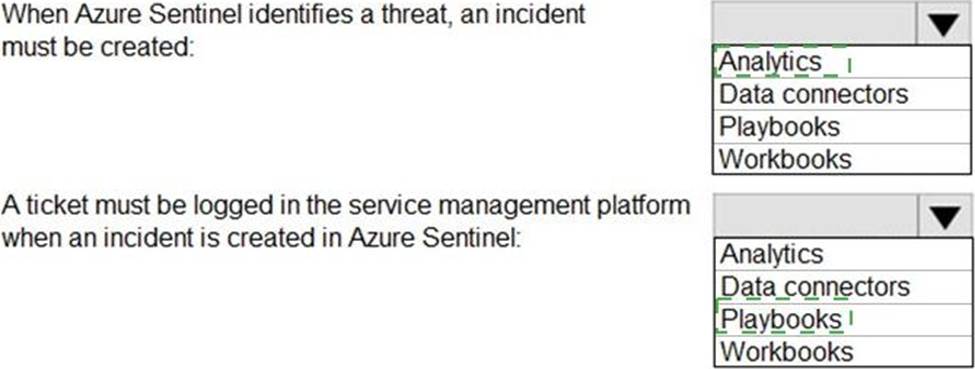
HOTSPOT
You have an Azure subscription that contains an Azure Sentinel workspace.
Azure Sentinel is configured to ingest logs from several Azure workloads. A third-party service management platform is used to manage incidents.
You need to identify which Azure Sentinel components to configure to meet the following requirements:
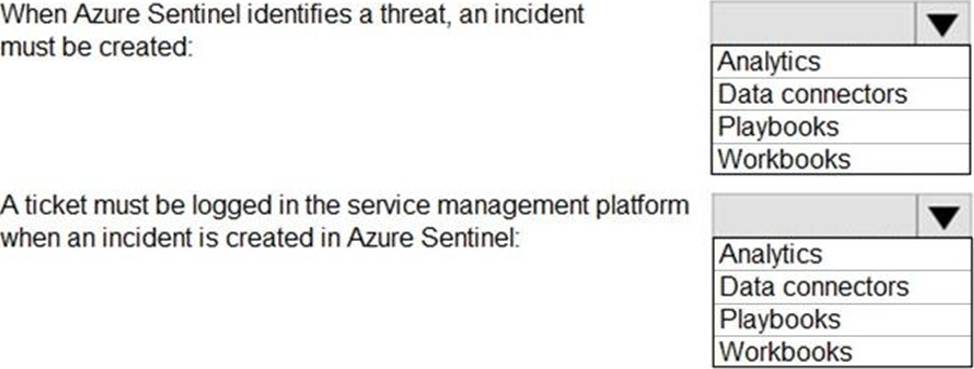
When Azure Sentinel identifies a threat, an incident must be created.
A ticket must be logged in the service management platform when an incident is created in Azure Sentinel.
Which component should you identify for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
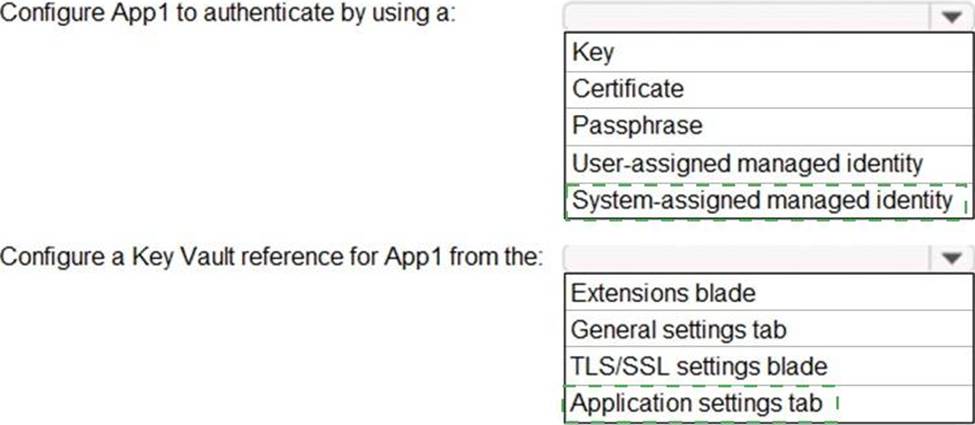
HOTSPOT
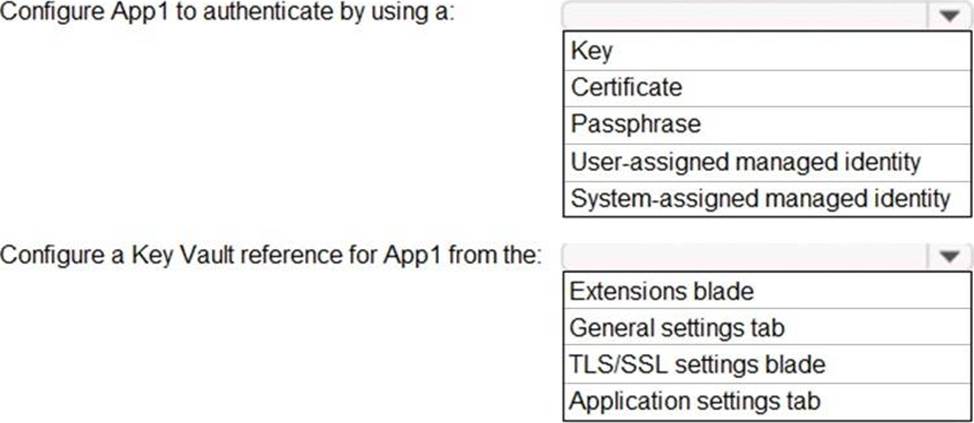
You have an Azure subscription that contains a web app named App1 and an Azure key vault named Vault1.
You need to configure App1 to store and access the secrets in Vault1.
How should you configure App1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You company has an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to create several security alerts by using Azure Monitor.
You need to prepare the Azure subscription for the alerts.
What should you create first?
- A . An Azure Storage account
- B . an Azure Log Analytics workspace
- C . an Azure event hub
- D . an Azure Automation account
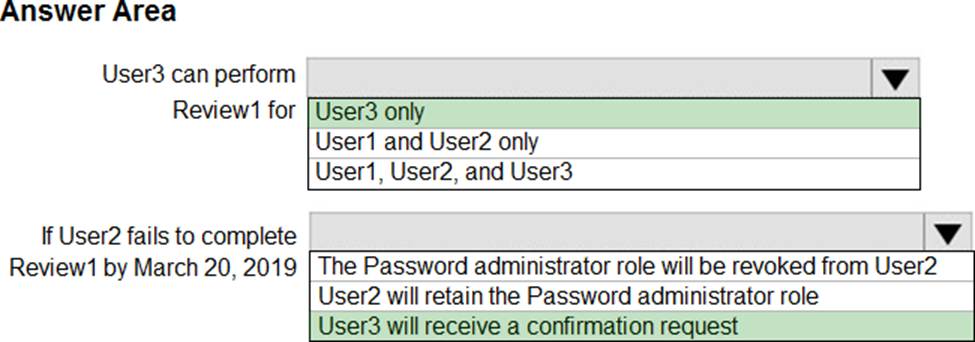
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
The tenant contains the users shown in the following table.
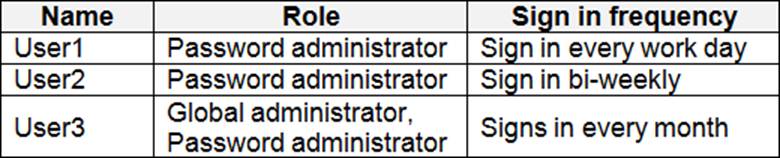
You configure an access review named Review1 as shown in the following exhibit.
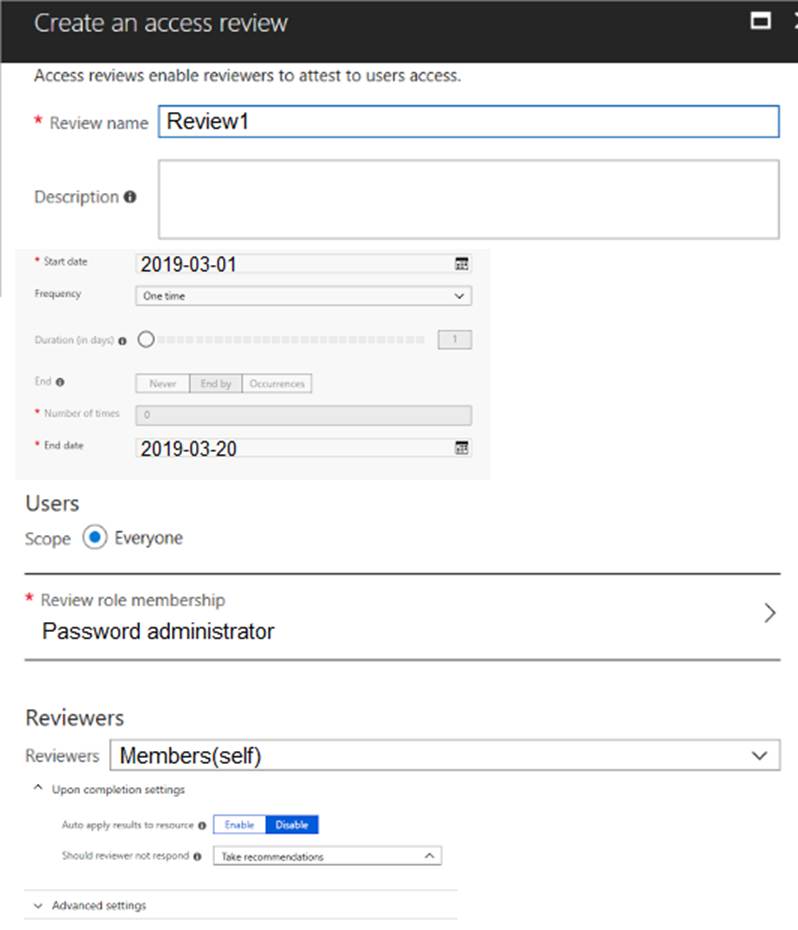
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
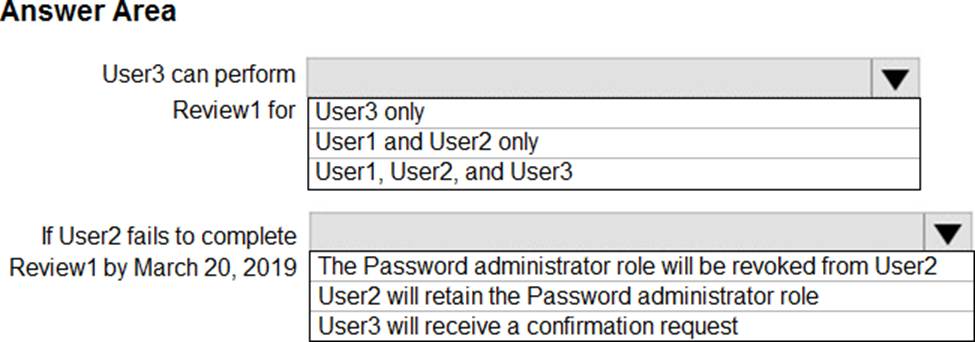
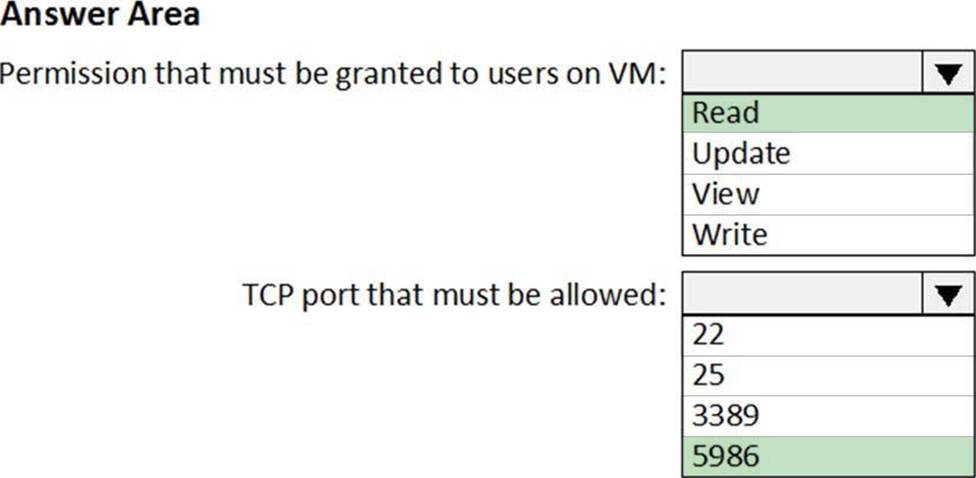
HOTSPOT
You are configuring just in time (JIT) VM access to a set of Azure virtual machines.
You need to grant users PowerShell access to the virtual machine by using JIT VM access.
What should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You plan to use Azure Resource Manager templates to perform multiple deployments of identically configured Azure virtual machines. The password for the administrator account of each deployment is stored as a secret in different Azure key vaults.
You need to identify a method to dynamically construct a resource ID that will designate the key vault
containing the appropriate secret during each deployment. The name of the key vault and the name of the
secret will be provided as inline parameters.
What should you use to construct the resource ID?
- A . a key vault access policy
- B . a linked template
- C . a parameters file
- D . an automation account
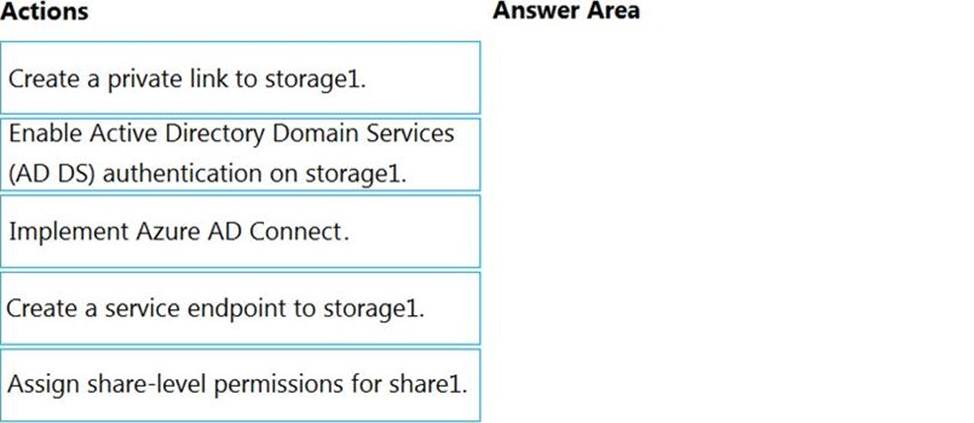
DRAG DROP
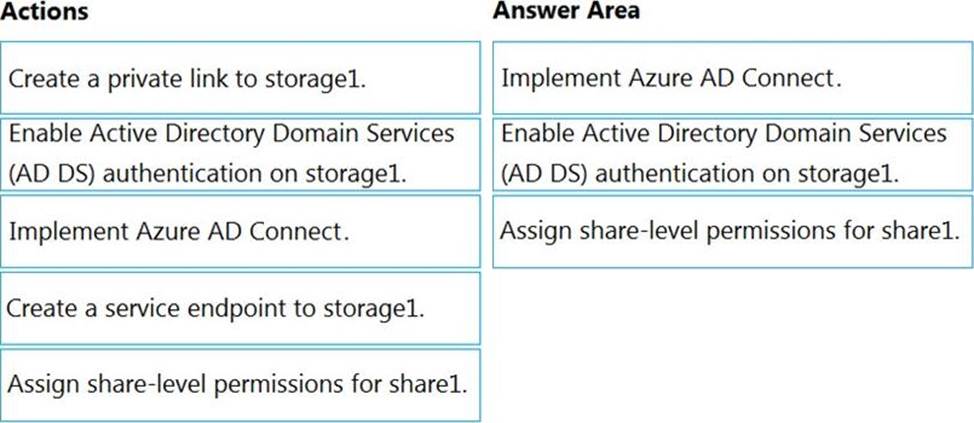
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains a user named User1.
You have an Azure subscription that is linked to an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains an Azure Storage account named storage1. Storage1 contains an Azure file share named share1.
Currently, the domain and the tenant are not integrated.
You need to ensure that User1 can access share1 by using his domain credentials.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You create a new Azure subscription.
You need to ensure that you can create custom alert rules in Azure Security Center.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Onboard Azure Active Directory (Azure AD) Identity Protection.
- B . Create an Azure Storage account.
- C . Implement Azure Advisor recommendations.
- D . Create an Azure Log Analytics workspace.
- E . Upgrade the pricing tier of Security Center to Standard.
You have an Azure subscription.
You plan to map an online infrastructure and perform vulnerability scanning for the following:
• ASNs
• Hostnames
• IP addresses
• SSL certificates What should you use?
- A . Microsoft Defender for Cloud
- B . Microsoft Defender for Identity
- C . Microsoft Defender for Endpoint
- D . Microsoft Defender External Attack Surface Management (Defender EASM)
You have the Azure resource shown in the following table.
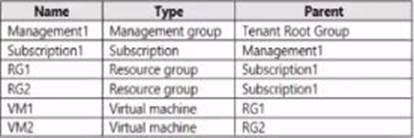
You need to meet the following requirements:
* Internet-facing virtual machines must be protected by using network security groups (NSGs).
* All the virtual machines must have disk encryption enabled.
What is the minimum number of security that you should create in Azure Security Center?
- A . 1
- B . 2
- C . 3
- D . 4