Microsoft AZ-500 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: AZ-500
- Prüfungsname: Microsoft Azure Security Technologies
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 02.02.2026
You have an Azure subscription that contains an Azure web app named 1 and a virtual machine named VM1. VM1 runs Microsoft SQL Server and is connected to a virtual network named VNet1.
App1, VM1, and Vent are in the US Central Azure region.
You need to ensure that App1 can connect to VM1. The solution must minimize costs.
- A . NAT gateway integration
- B . Azure Front Door
- C . regional virtual network integration
- D . gateway-required virtual network integration
- E . Azure Application Gateway integration
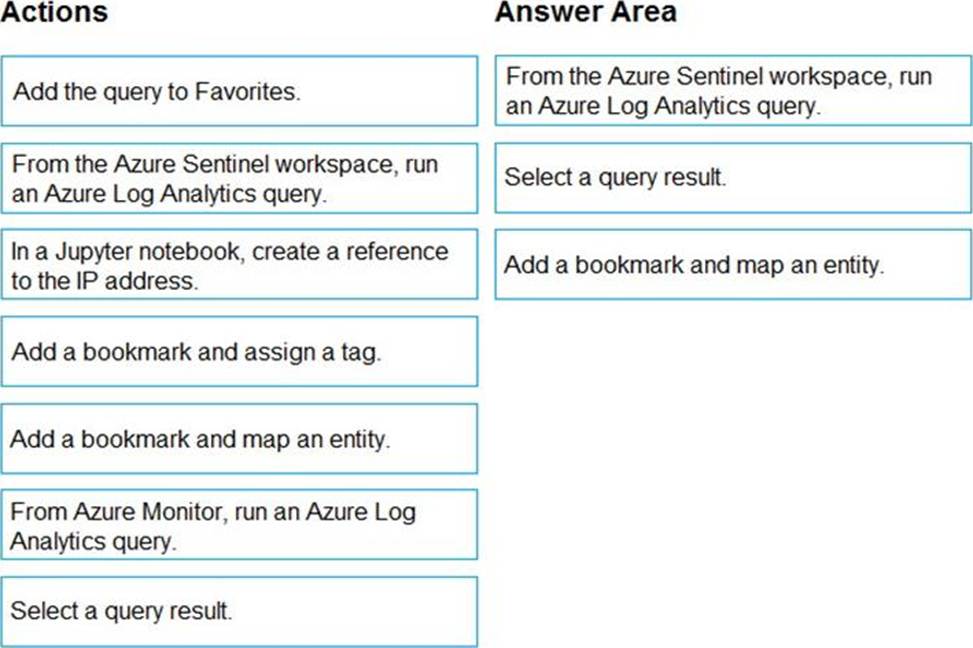
DRAG DROP
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) data connector.
You are threat hunting suspicious traffic from a specific IP address.
You need to annotate an intermediate event stored in the workspace and be able to reference the IP address when navigating through the investigation graph.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
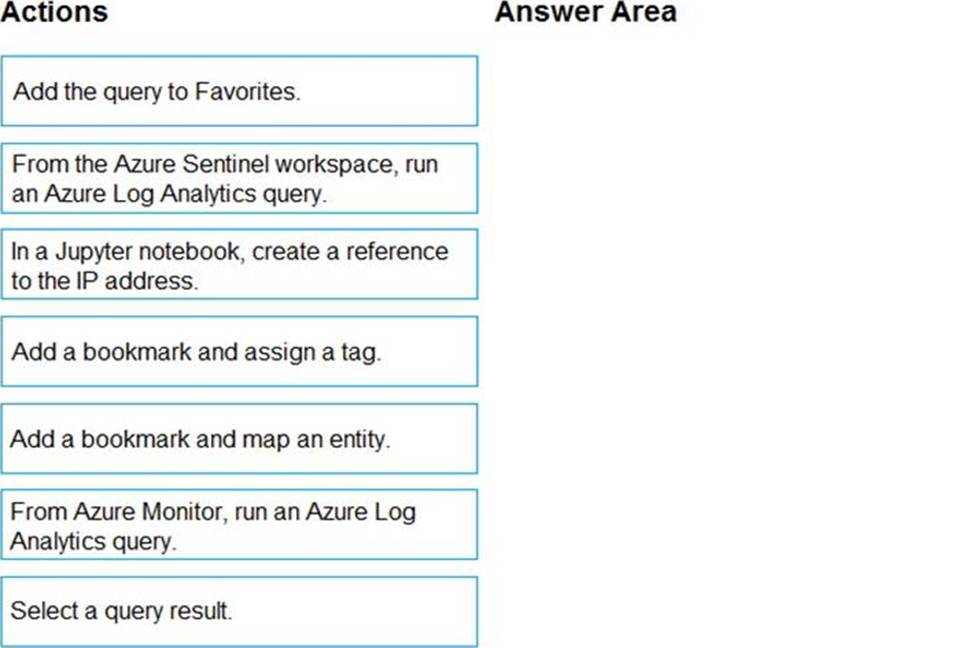
You have an Azure Active Directory (Azure AD) tenant.
You have the deleted objects shown in the following table.
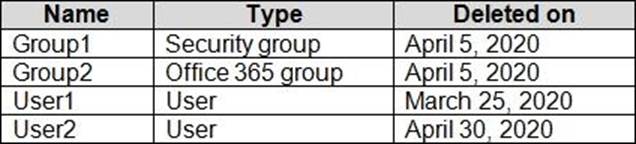
On May 4, 2020, you attempt to restore the deleted objects by using the Azure Active Directory admin center.
Which two objects can you restore? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Group1
- B . Group2
- C . User2
- D . User1
SIMULATION
Lab Task
Task 4
You need to ensure that when administrators deploy resources by using an Azure Resource Manager template, the deployment can access secrets in an Azure key vault named KV31330471.
You have an Azure Sentinel deployment.
You need to create a scheduled query rule named Rule1.
What should you use to define the query rule logic for Rule1?
- A . a Transact-SQL statement
- B . a JSON definition
- C . GraphQL
- D . a Kusto query
Which of these services is NOT involved in controlling network traffic to and from Azure resources?
- A . Azure Firewalls
- B . Network Security Groups
- C . Azure Front Door
- D . Azure Active Directory
You have an Azure subscription named Sub1. Sub1 contains a virtual network named VNet1 that contains one subnet named Subnet1.
Subnet1 contains an Azure virtual machine named VM1 that runs Ubuntu Server 20.04.
You create a service endpoint for Microsoft. Storage in Subnet1.
You need to ensure that when you deploy Docker containers to VM1, the containers can access Azure Storage resources by using the service endpoint.
What should you do on VM1 before you deploy the container?
- A . Create an application security group and a network security group (NSG).
- B . Install the container network interface (CNI) plug-in.
- C . Edit the docker-compose.ym1 file.
You have an Azure subscription that uses Microsoft Defender for Cloud.
You have an Amazon Web Services (AWS) account.
You need to add the AWS account to Defender for Cloud.
What should you do first?
- A . From the Azure portal, add the AWS enterprise application.
- B . From the AWS account, enable a security hub.
- C . From Defender for Cloud, configure the Security solutions settings.
- D . From Defender for Cloud, configure the Environment settings.
You have an Azure subscription that uses Microsoft Defender for Cloud.
You have an Amazon Web Services (AWS) account.
You need to add the AWS account to Defender for Cloud.
What should you do first?
- A . From the Azure portal, add the AWS enterprise application.
- B . From the AWS account, enable a security hub.
- C . From Defender for Cloud, configure the Security solutions settings.
- D . From Defender for Cloud, configure the Environment settings.
You have an Azure subscription that contains the resources shown in the following table.
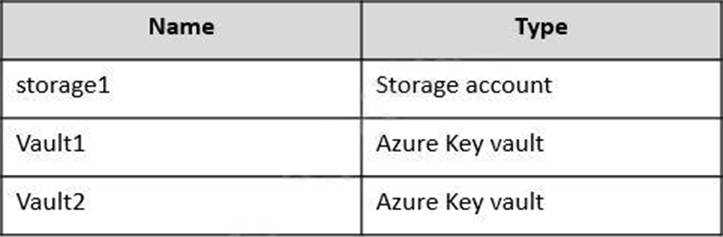
You plan to deploy the virtual machines shown in the following table.
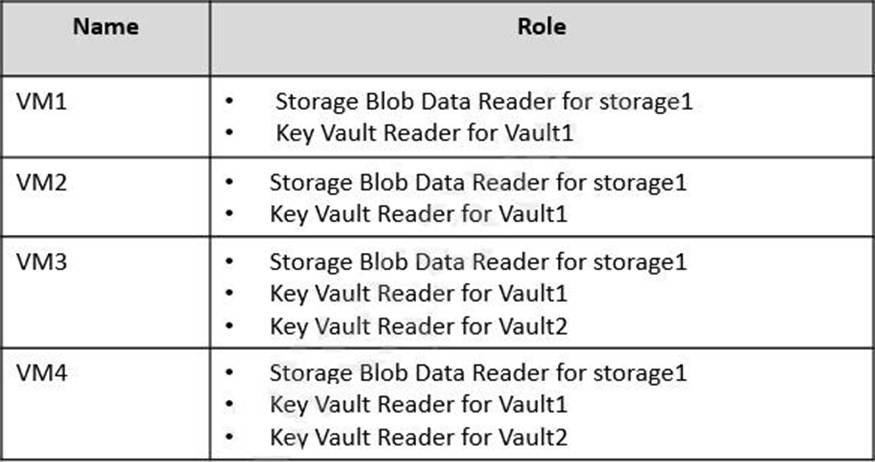
You need to assign managed identities to the virtual machines.
The solution must meet the following requirements:
– Assign each virtual machine the required roles.
– Use the principle of least privilege.
What is the minimum number of managed identities required?
- A . 1
- B . 2
- C . 3
- D . 4