Microsoft AZ-500 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: AZ-500
- Prüfungsname: Microsoft Azure Security Technologies
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 02.02.2026
You have an Azure subscription that contains a Microsoft Defender External Attack Surface Management (Defender EASM) resource named EASM1. EASM1 has discovery enabled and contains several inventory assets.
You need to identify which inventory assets are vulnerable to the most critical web app security risks.
Which Defender EASM dashboard should you use?
- A . Attack Surface Summary
- B . GDPRCompliance
- C . Security Posture
- D . OWASPToplO
HOTSPOT
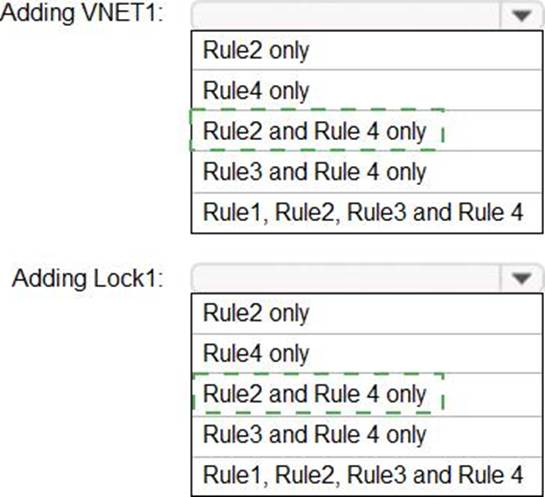
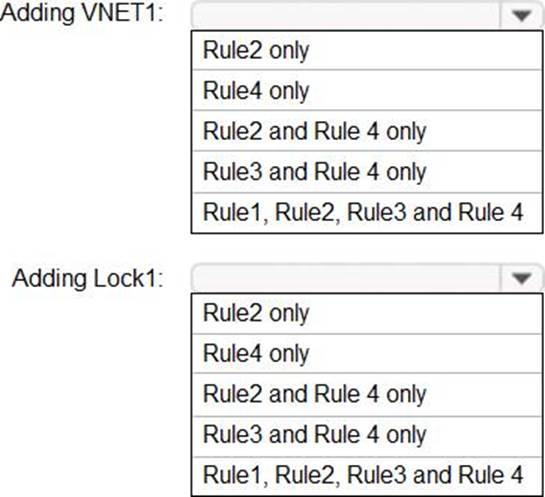
You have an Azure subscription that contains a user named Admin1 and a resource group named RG1.
In Azure Monitor, you create the alert rules shown in the following table.
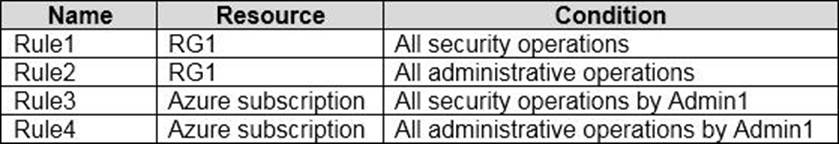
Admin1 performs the following actions on RG1:
– Adds a virtual network named VNET1
– Adds a Delete lock named Lock1
Which rules will trigger an alert as a result of the actions of Admin1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You plan to create a custom role-based access control (RBAC) role that will provide permission to read the Azure Storage account.
Which property of the RBAC role definition should you configure?
- A . NotActions []
- B . DataActions []
- C . AssignableScopes []
- D . Actions []
DRAG DROP
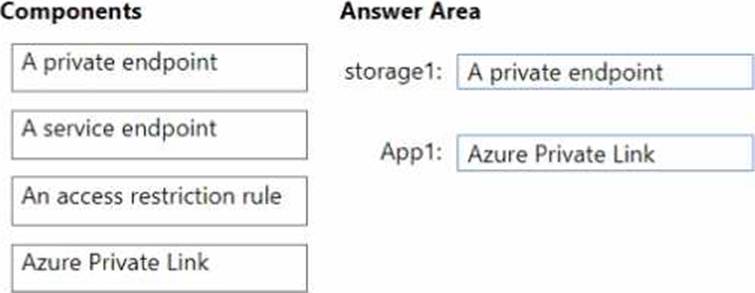
You have an on-premises datacenter.
You have an Azure subscription that contains a virtual machine named VM1. VM1 is connected to a virtual network named VNet1. VNet1 is connected to the on-premises datacenter by using a Site-to-Site (S2S) VPN.
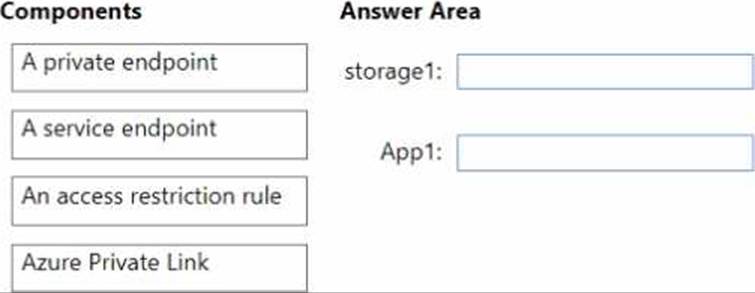
You plan to create an Azure storage account named storage1 and deploy an Azure web app named App1.
You need to ensure that network communication to each resource meets the following requirements:
• Connections to App1 must be allowed only from corporate network NAT addresses.
• Connections from VNet1 to storage1 must use the Microsoft backbone network.
• The solution must minimize costs.
What should you configure for each resource? To answer, drag the appropriate components to the correct resources. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains the resources shown in the following table.
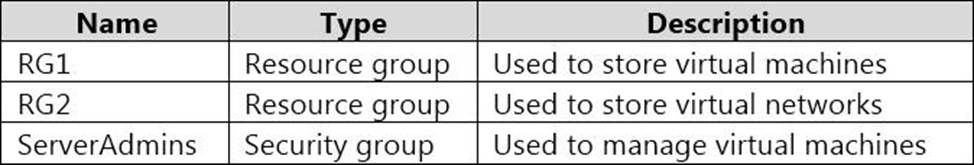
You need to ensure that ServerAdmins can perform the following tasks:
– Create virtual machines in RG1 only.
– Connect the virtual machines to the existing virtual networks in RG2 only.
The solution must use the principle of least privilege.
Which two role-based access control (RBAC) roles should you assign to ServerAdmins? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . a custom RBAC role for RG2
- B . the Network Contributor role for RG2
- C . the Contributor role for the subscription
- D . a custom RBAC role for the subscription
- E . the Network Contributor role for RG1
- F . the Virtual Machine Contributor role for RG1
You have an Azure subscription that contains a virtual network.
The virtual network contains the subnets shown in the following table.

The subscription contains the virtual machines shown in the following table.

You enable just in time (JIT) VM access for all the virtual machines.
You need to identify which virtual machines are protected by JIT.
Which virtual machines should you identify?
- A . VM4 only
- B . VM1 and VM3 only
- C . VM1, VM3 and VM4 only
- D . VM1, VM2, VM3, and VM4
Which Azure service provides threat protection for virtual machines, SQL databases, and Azure Storage?
- A . Azure Security Center
- B . Azure Monitor
- C . Azure Defender
- D . Azure Sentinel
You have an Azure subscription that contains the virtual machines shown in the following table.
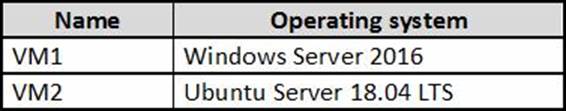
From Azure Security Center, you turn on Auto Provisioning.
You deploy the virtual machines shown in the following table.
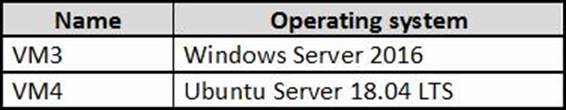
On which virtual machines is the Microsoft Monitoring agent installed?
- A . VM3 only
- B . VM1 and VM3 only
- C . VM3 and VM4 only
- D . VM1, VM2, VM3, and VM4
You have the Azure virtual machines shown in the following table.
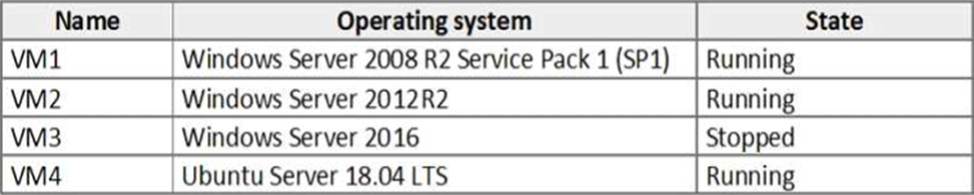
For which virtual machine can you enable Update Management?
- A . VM2 and VM3 only
- B . VM2, VM3, and VM4 only
- C . VM1, VM2, and VM4 only
- D . VM1, VM2, VM3, and VM4
- E . VM1, VM2, and VM3 only
You have a web app named WebApp1.
You create a web application firewall (WAF) policy named WAF1.
You need to protect WebApp1 by using WAF1.
What should you do first?
- A . Deploy an Azure Front Door.
- B . Add an extension to WebApp1.
- C . Deploy Azure Firewall.