Microsoft AZ-500 Übungsprüfungen
Zuletzt aktualisiert am 03.02.2026- Prüfungscode: AZ-500
- Prüfungsname: Microsoft Azure Security Technologies
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 03.02.2026
HOTSPOT
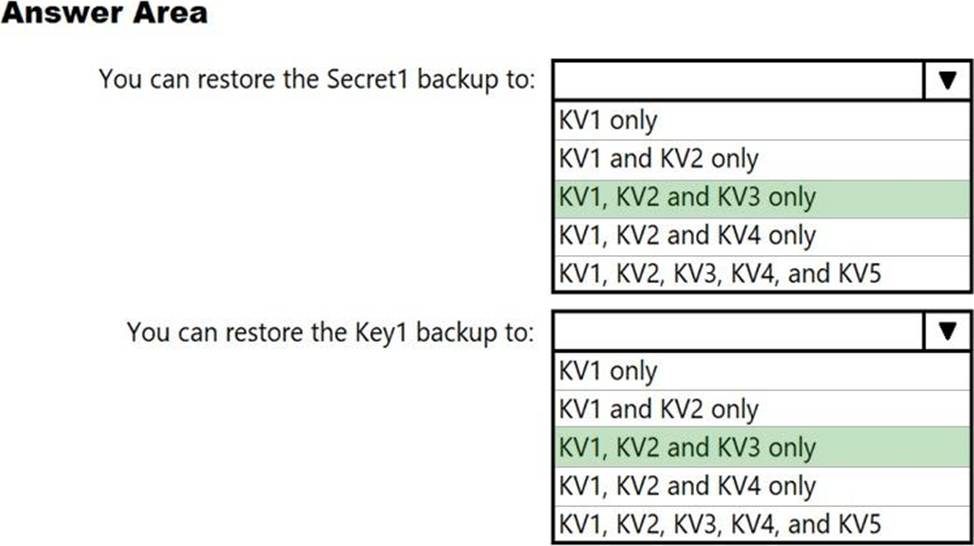
You have the Azure key vaults shown in the following table.
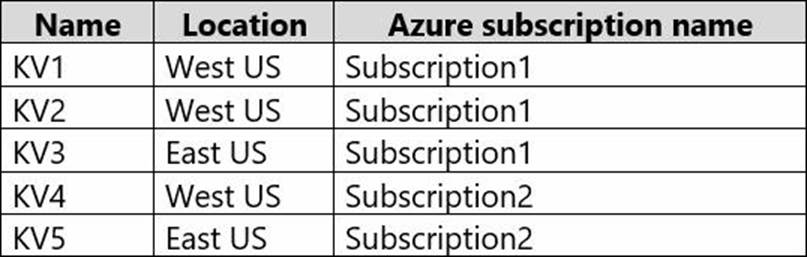
KV1 stores a secret named Secret1 and a key for a managed storage account named Key1.
You back up Secret1 and Key1.
To which key vaults can you restore each backup? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Storage account named storage1 that has a container named container1. You need to prevent the blobs in container1 from being modified.
What should you do?
- A . From container1, change the access level.
- B . From container1 add an access policy.
- C . From container1, modify the Access Control (1AM) settings.
- D . From storage1, enable soft delete for blobs.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a hybrid configuration of Azure Active Directory (AzureAD).
You have an Azure HDInsight cluster on a virtual network.
You plan to allow users to authenticate to the cluster by using their on-premises Active Directory credentials.
You need to configure the environment to support the planned authentication.
Solution: You deploy the On-premises data gateway to the on-premises network.
Does this meet the goal?
- A . Yes
- B . No
You company has an Azure subscription named Sub1. Sub1 contains an Azure web app named
WebApp1 that uses Azure Application Insights. WebApp1 requires users to authenticate by using
OAuth 2.0 client secrets.
Developers at the company plan to create a multi-step web test app that preforms synthetic transactions emulating user traffic to Web App1.
You need to ensure that web tests can run unattended.
What should you do first?
- A . In Microsoft Visual Studio, modify the .webtest file.
- B . Upload the .webtest file to Application Insights.
- C . Register the web test app in Azure AD.
- D . Add a plug-in to the web test app.
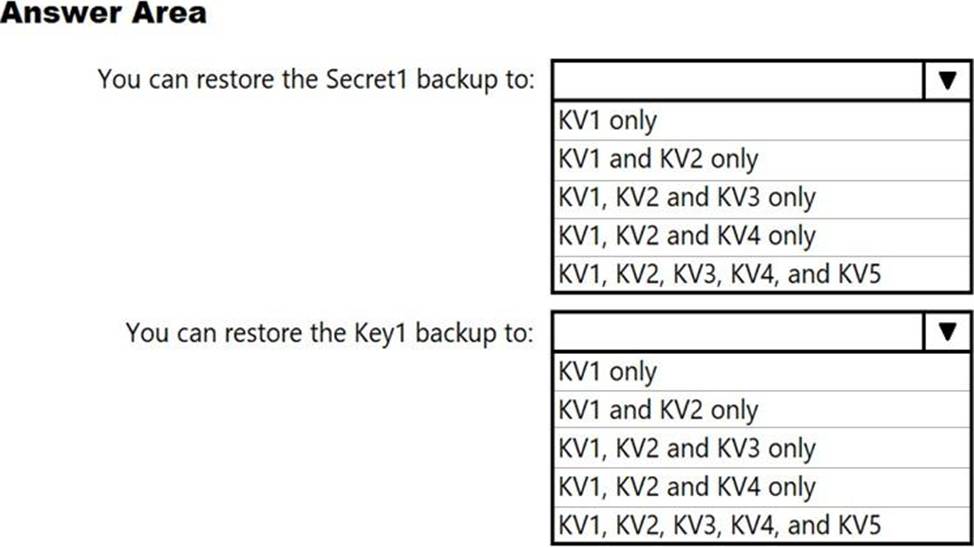
HOTSPOT
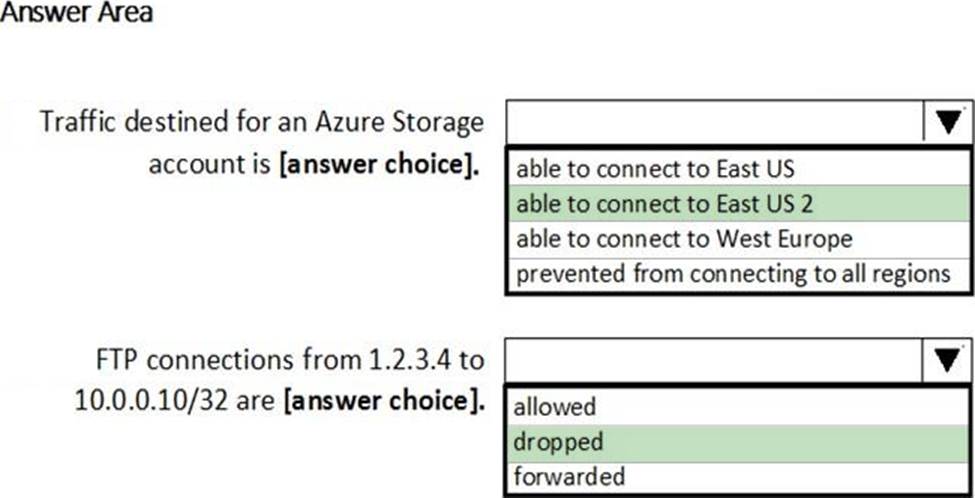
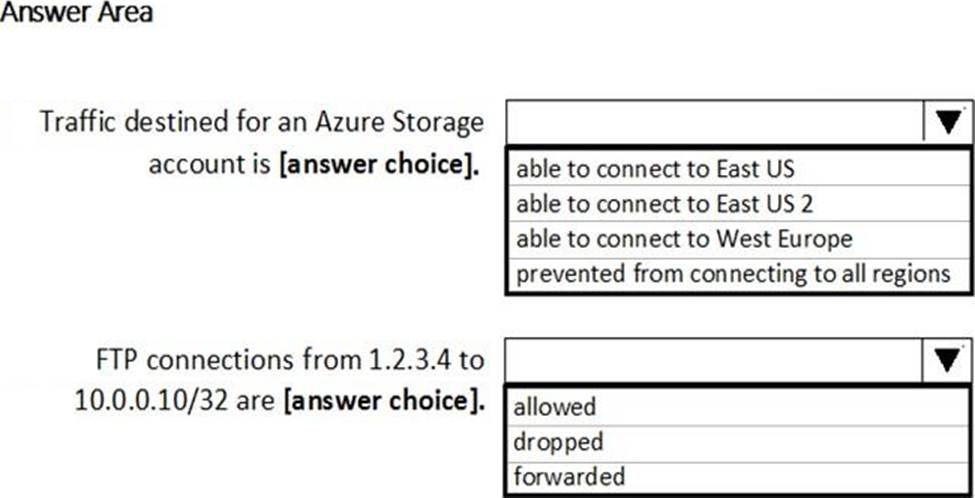
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzureRmNetworkSecurityRuleConfig and receive the output shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
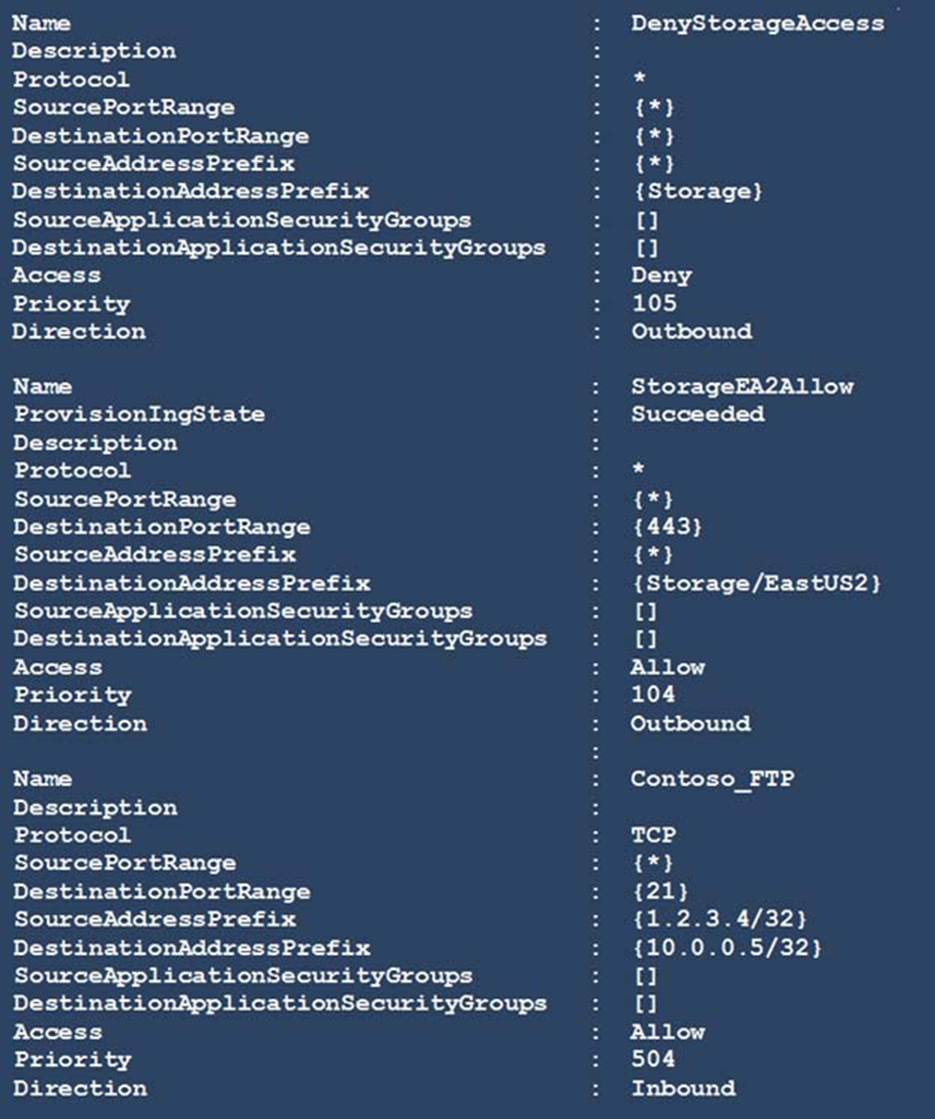
HOTSPOT
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzureRmNetworkSecurityRuleConfig and receive the output shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.

HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains two users named User1 and
User2 and a registered app named App1.
You create an app-specific role named Role1.
You need to assign Role1 to User1 and enable User2 to request access to App1.
Which two settings should you modify? To answer select the appropriate settings in the answer area NOTE: Each correct selection is worth one pant.
You plan to create an Azure Kubernetes Service (AKS) cluster in an Azure subscription.
The manifest of the registered server application is shown in the following exhibit.
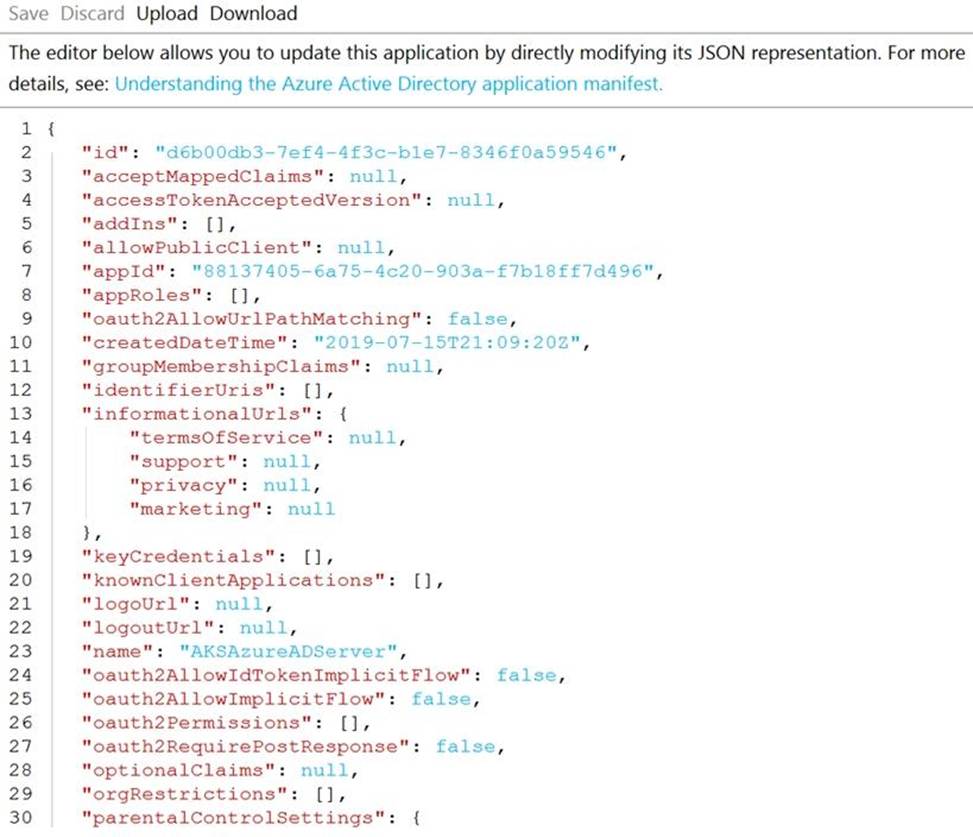
You need to ensure that the AKS cluster and Azure Active Directory (Azure AD) are integrated.
Which property should you modify in the manifest?
- A . accessTokenAcceptedVersion
- B . keyCredentials
- C . groupMembershipClaims
- D . acceptMappedClaims
You have an Azure subscription that contains the virtual machines shown in the following table.
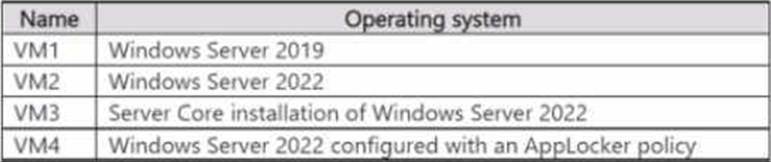
You are configuring Microsoft Defender for Servers.
You plan to enable adaptive application controls to create an allowlist of known-safe apps on the virtual machines.
Which virtual machines support the use of adaptive application controls?
- A . VM1 and VM2 only
- B . VM2 and VM4 only
- C . VM2 and VM3 only
- D . VM1, VM2, VM3, and VM4
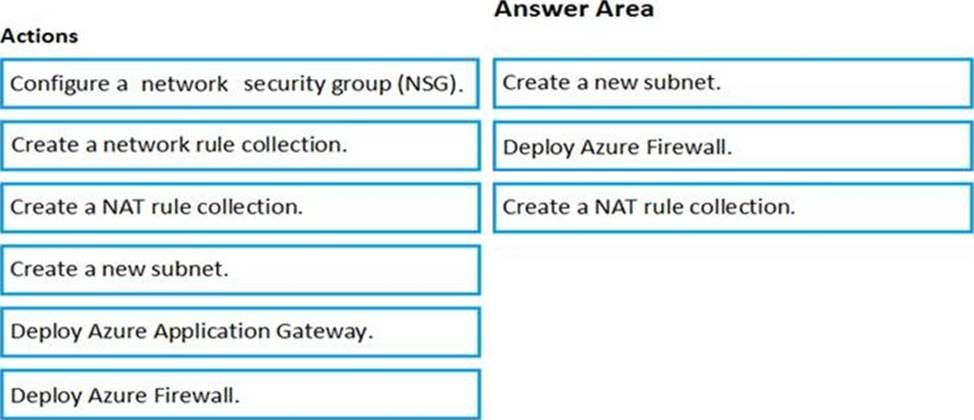
DRAG DROP
You have an Azure subscription that contains the following resources:
– A virtual network named VNET1 that contains two subnets named Subnet1 and Subnet2.
– A virtual machine named VM1 that has only a private IP address and connects to Subnet1.
You need to ensure that Remote Desktop connections can be established to VM1 from the internet.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order.