Microsoft AZ-500 Übungsprüfungen
Zuletzt aktualisiert am 03.02.2026- Prüfungscode: AZ-500
- Prüfungsname: Microsoft Azure Security Technologies
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 03.02.2026
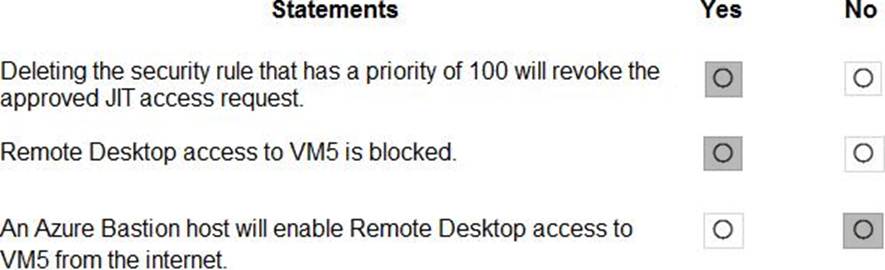
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
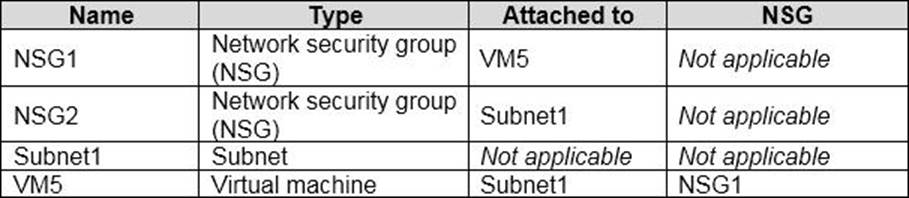
An IP address of 10.1.0.4 is assigned to VM5. VM5 does not have a public IP address.
VM5 has just in time (JIT) VM access configured as shown in the following exhibit.
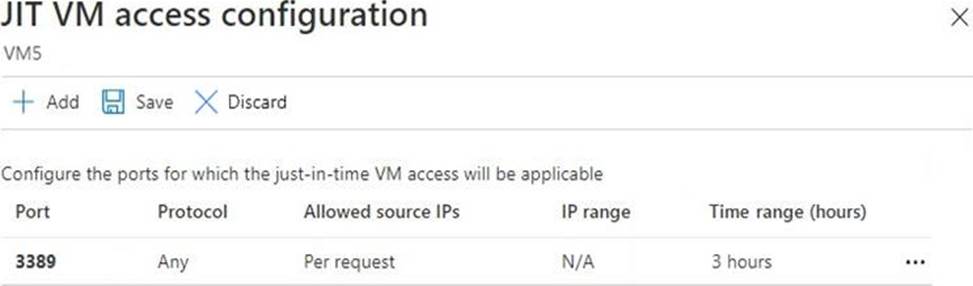
You enable JIT VM access for VM5.
NSG1 has the inbound rules shown in the following exhibit.
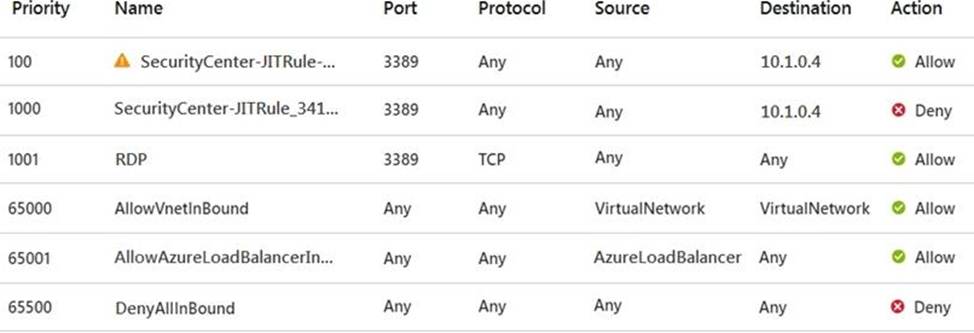
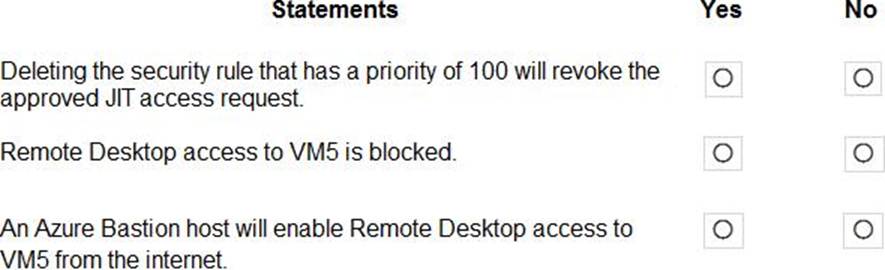
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a user named UseR1.
You need to ensure that UseR1 can perform the following tasks:
• Create groups.
• Create access reviews for role-assignable groups.
• Assign Azure AD roles to groups.
The solution must use the principle of least privilege.
Which role should you assign to User1?
- A . Groups administrator
- B . Authentication administrator
- C . Identity Governance Administrator
- D . Privileged role administrator
You have an Azure subscription that contains the Azure virtual machines shown in the following table.
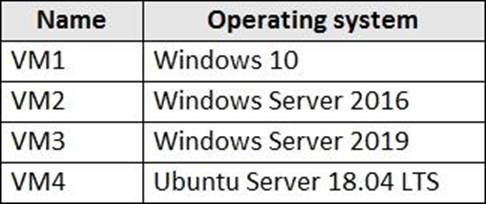
You create an MDM Security Baseline profile named Profile1.
You need to identify to which virtual machines Profile1 can be applied.
Which virtual machines should you identify?
- A . VM1 only
- B . VM1, VM2, and VM3 only
- C . VM1 and VM3 only
- D . VM1, VM2, VM3, and VM4
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center for the centralized policy management of three Azure subscriptions.
You use several policy definitions to manage the security of the subscriptions.
You need to deploy the policy definitions as a group to all three subscriptions.
Solution: You create an initiative and an assignment that is scoped to the Tenant Root Group management group.
Does this meet the goal?
- A . Yes
- B . No
You have an Azure subscription that contains an Azure App Service app named App1, an Azure container instance named AC1. and a storage account named storage1. AC1 hosts an app named App2.
Users send requests to App1 by using a URL of https:/app1.contoso.com/echo/resource-cache? param1 =sample. App1 calls App2. which retrieves data from storage1.
You need to ensure that a security alert will be generated when connections are detected from anomalous IP addresses.
Which Microsoft Defender for Cloud service should you use?
- A . Microsoft Defender for App Service
- B . Microsoft Defender for APIs
- C . Microsoft Defender for Storage
- D . Microsoft Defender for Containers
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a hybrid configuration of Azure Active Directory (Azure AD).
You have an Azure HDInsight cluster on a virtual network.
You plan to allow users to authenticate to the cluster by using their on-premises Active Directory credentials.
You need to configure the environment to support the planned authentication.
Solution: You deploy Azure Active Directory Domain Services (Azure AD DS) to the Azure subscription.
Does this meet the goal?
- A . Yes
- B . No
You have an Azure web app named webapp1.
You need to configure continuous deployment for webapp1 by using an Azure Repo.
What should you create first?
- A . an Azure Application Insights service
- B . an Azure DevOps organizations
- C . an Azure Storage account
- D . an Azure DevTest Labs lab
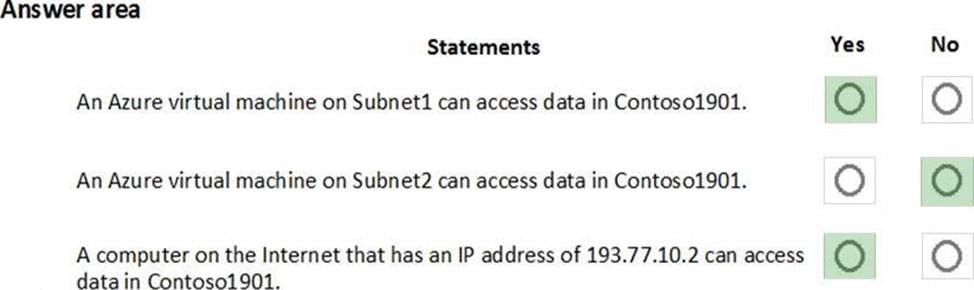
HOTSPOT
You create resources in an Azure subscription as shown in the following table.
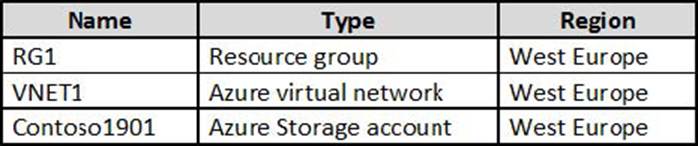
VNET1 contains two subnets named Subnet1 and Subnet2. Subnet1 has a network ID of 10.0.0.0/24.
Subnet2 has a network ID of 10.1.1.0/24.
Contoso1901 is configured as shown in the exhibit. (Click the Exhibit tab.)
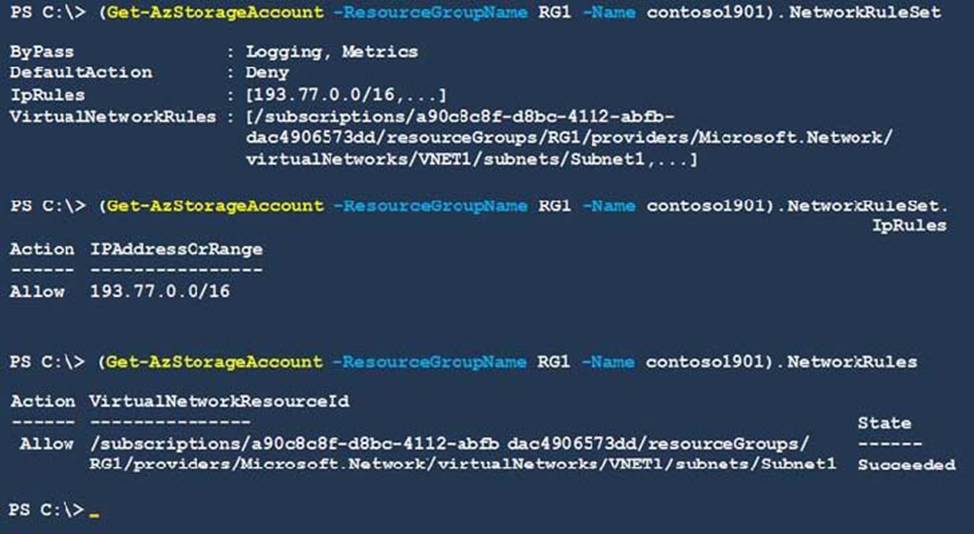
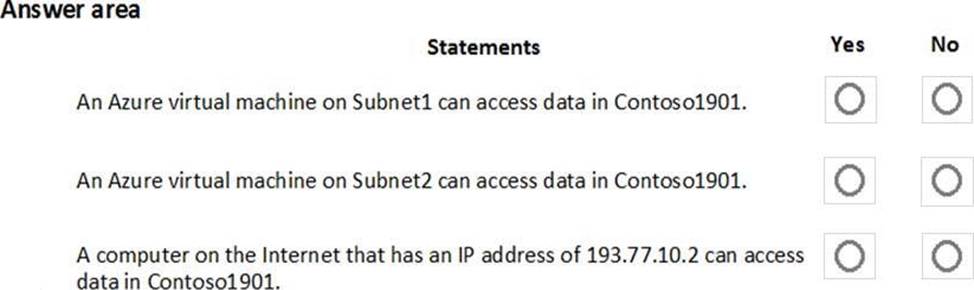
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have 10 on-premises servers that run Windows Server 2019.
You plan to implement Azure Security Center vulnerability scanning for the servers.
What should you install on the servers first?
- A . the Security Events data connector in Azure Sentinel
- B . the Microsoft Endpoint Configuration Manager client
- C . the Azure Arc enabled servers Connected Machine agent
- D . the Microsoft Defender for Endpoint agent
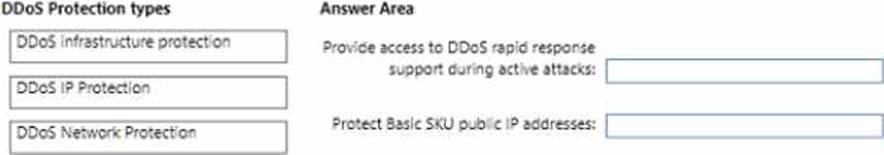
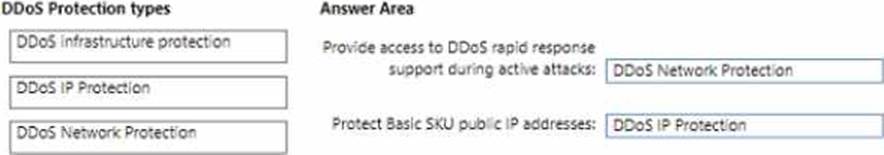
DRAG DROP
You have an Azure subscription.
You plan to implement Azure DDoS Protection.
The solution must meet the following requirement:
* Provide access to DDoS rapid response support during active attacks.
* Project Basic SKU public IP addresses.
You need to recommend which type of DDoS projection to use for each requirement.
What should you recommend? To answer, drag the appropriate DDoS projection types to the correct requirements. Each DDoS Projection type may be used once, or not at all. You may need to drag the split bar between panes or scroll to view connect. NOTE: Each correct selection is worth one point.