Microsoft AZ-500 Übungsprüfungen
Zuletzt aktualisiert am 03.02.2026- Prüfungscode: AZ-500
- Prüfungsname: Microsoft Azure Security Technologies
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 03.02.2026
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sa1 by using several shared access signatures (SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to Sa1.
Solution: You create a lock on Sa1.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
You have an Azure subscription.
You plan to deploy the virtual machines shown in the following table.
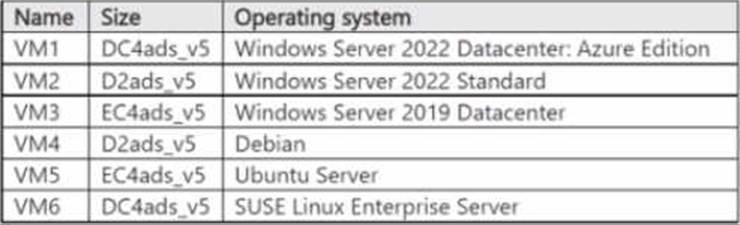
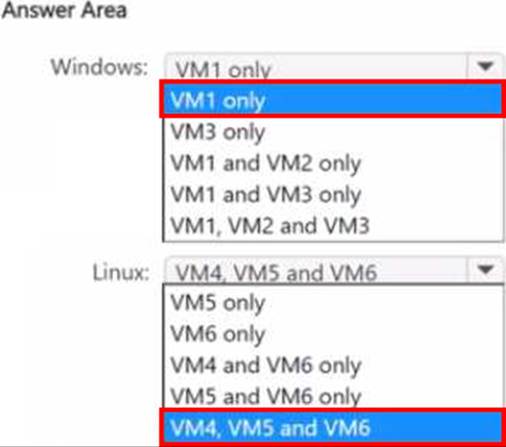
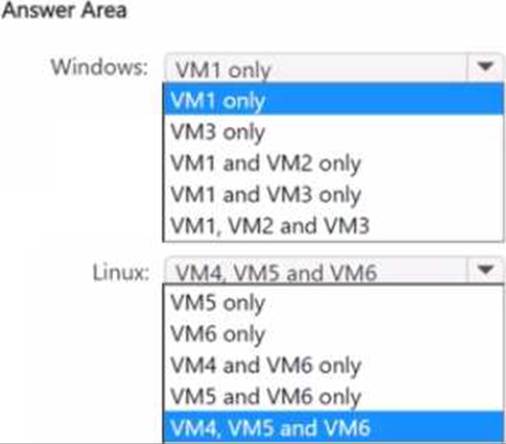
You need to identify the virtual machines and operating systems that can be deployed as confidential virtual machines?
Which Windows virtual machines and which Linux virtual machines should you identify?
HOTSPOT
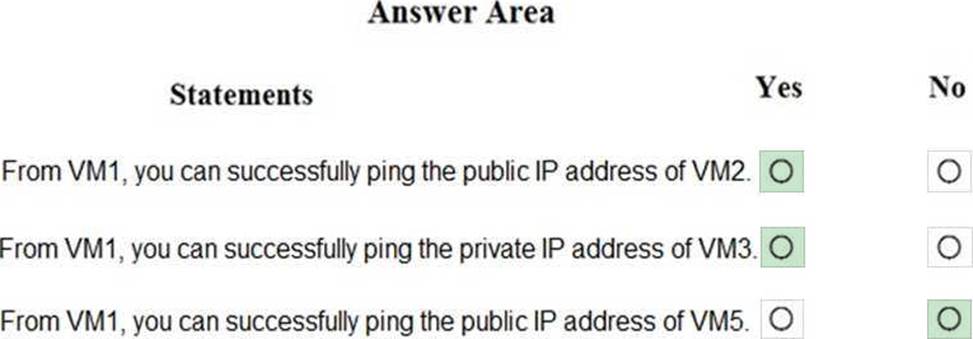
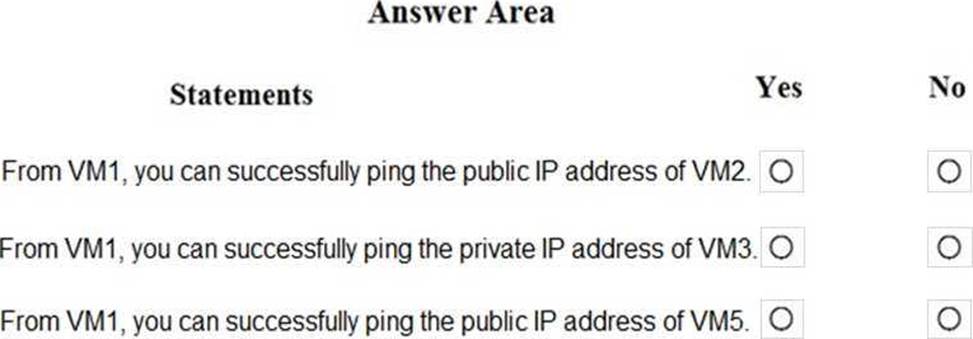
You are evaluating the security of the network communication between the virtual machines in Sub2.
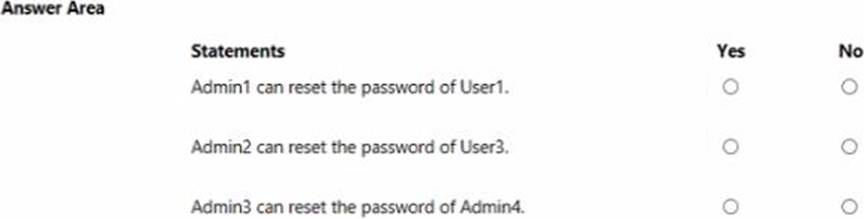
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
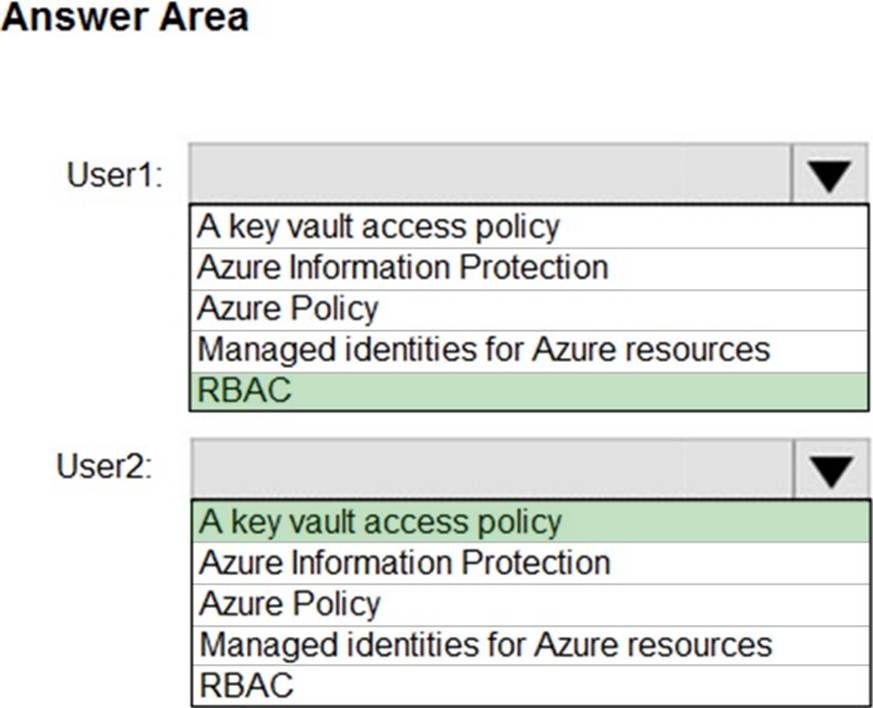
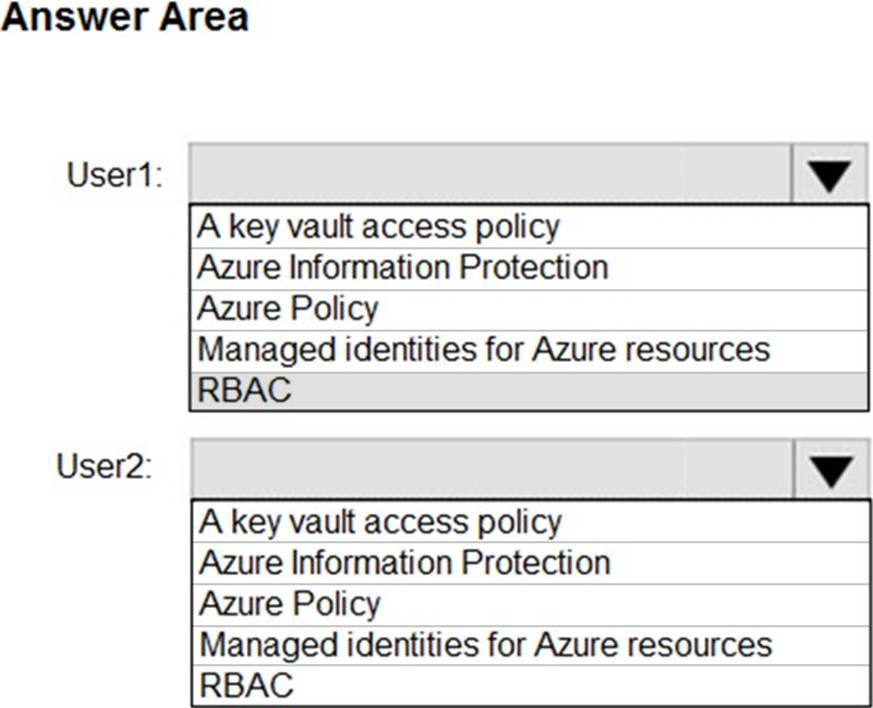
You have an Azure key vault.
You need to delegate administrative access to the key vault to meet the following requirements:
– Provide a user named User1 with the ability to set advanced access policies for the key vault.
– Provide a user named User2 with the ability to add and delete certificates in the key vault.
– Use the principle of least privilege.
What should you use to assign access to each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use the automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry.
What should you create?
- A . an Azure AD user
- B . a secret in Azure Key Vault
- C . an Azure AD group
- D . a role assignment
HOTSPOT
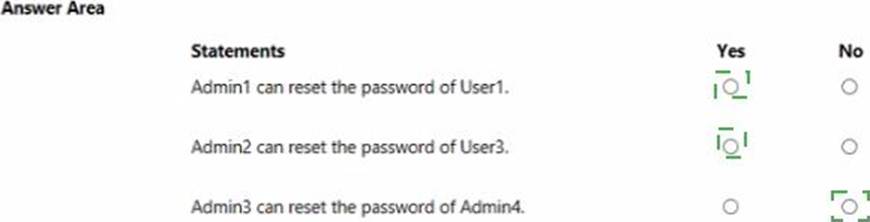
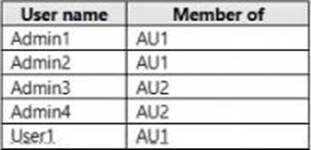
You have an Azure Active Directory (Azure AD) tenant that contains two administrative units named AU1 and AU2.
Users are assigned to the administrative units as shown in the following table.
You have a Microsoft Sentinel deployment.
You need to connect a third-party security solution to the deployment. The third-party solution will send Common Event Format (CER-formatted messages.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You have a Microsoft Sentinel deployment.
You need to connect a third-party security solution to the deployment. The third-party solution will send Common Event Format (CER-formatted messages.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

DRAG DROP
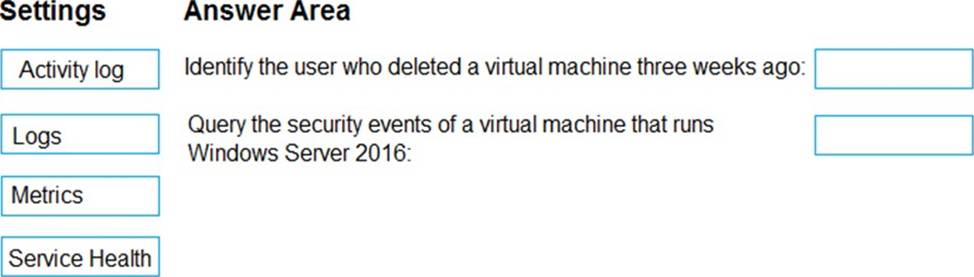
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines.
You are planning the monitoring of Azure services in the subscription.
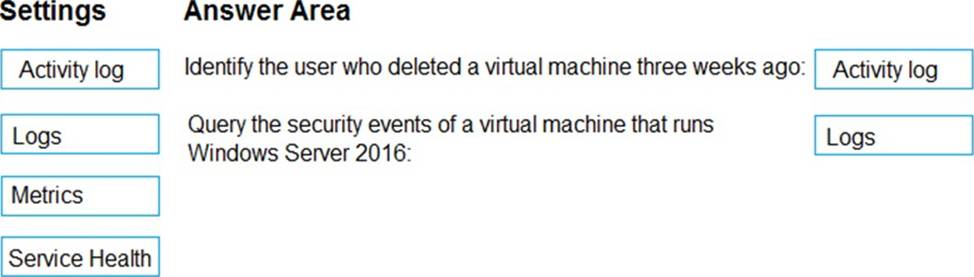
You need to retrieve the following details:
– Identify the user who deleted a virtual machine three weeks ago.
– Query the security events of a virtual machine that runs Windows Server 2016.
What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have an Azure subscription named Sub1 that contains the Azure key vaults shown in the following table.
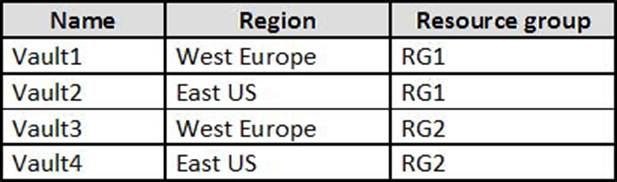
In Sub1, you create a virtual machine that has the following configurations:
• Name:VM1
• Size: DS2v2
• Resource group: RG1
• Region: West Europe
• Operating system: Windows Server 2016
You plan to enable Azure Disk Encryption on VM1.
In which key vaults can you store the encryption key for VM1?
- A . Vault1 or Vault3 only
- B . Vault1, Vault2, Vault3, or Vault4
- C . Vault1 only
- D . Vault1 or Vault2 only