Microsoft MS-102 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: MS-102
- Prüfungsname: Microsoft 365 Administrator
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 02.02.2026
HOTSPOT
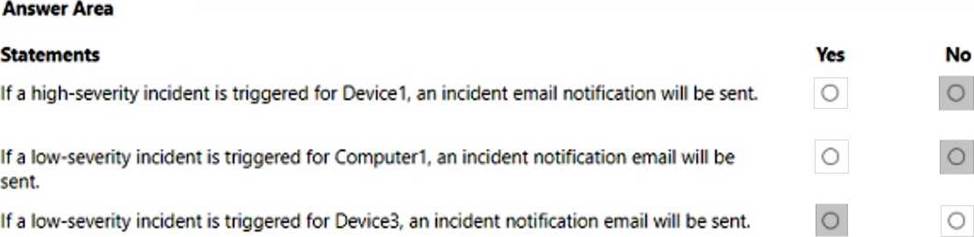
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and contains the devices shown in the following table.
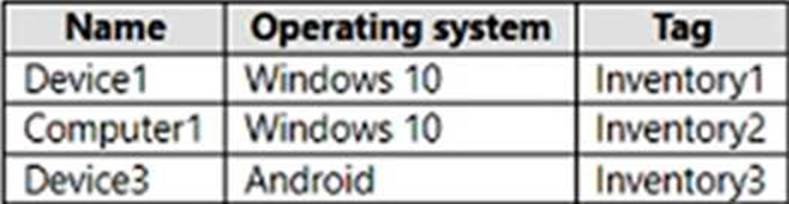
Defender for Endpoint has the device groups shown in the following table.
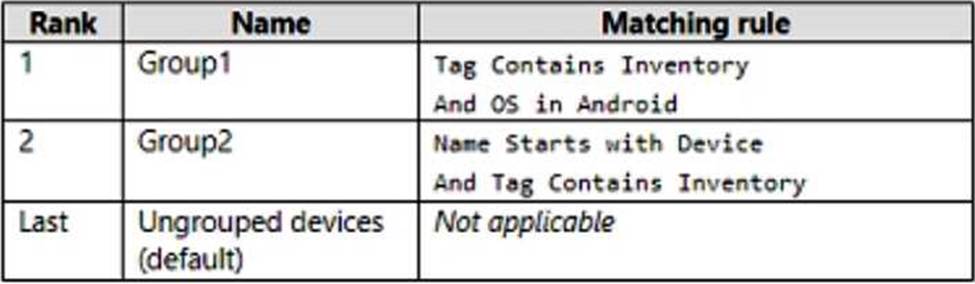
You create an incident email notification rule configured as shown in the following table.
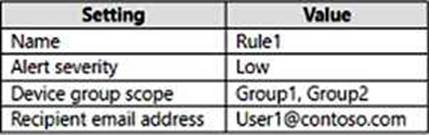
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
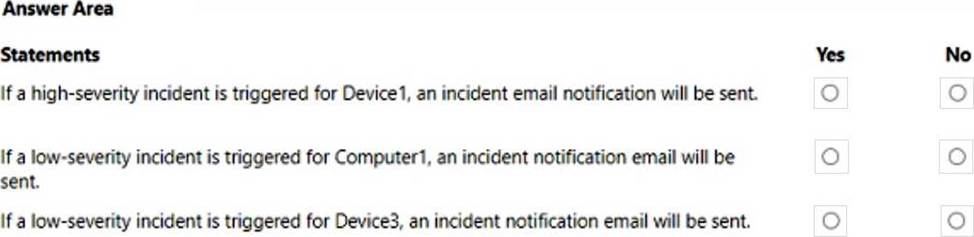
HOTSPOT
Your company uses Microsoft Defender for Endpoint.
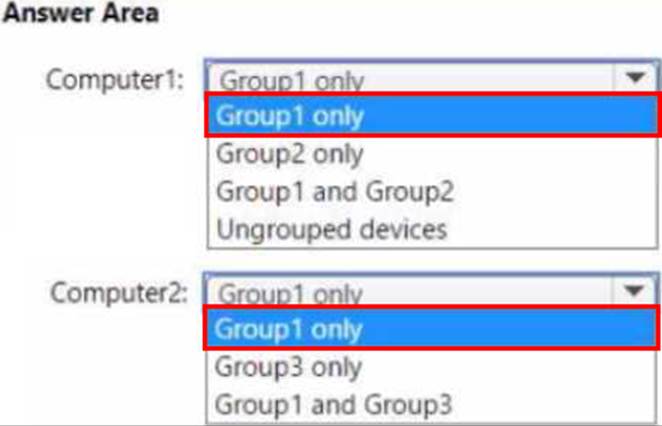
Microsoft Defender for Endpoint contains the device groups shown in the following table.
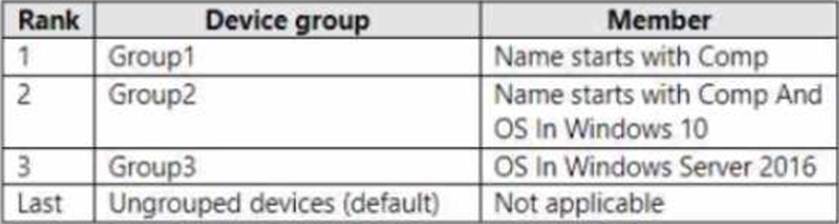
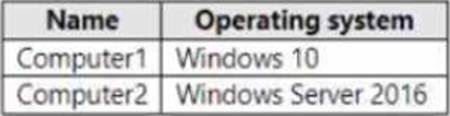
You onboard computers to Microsoft Defender for Endpoint as shown in the following table.
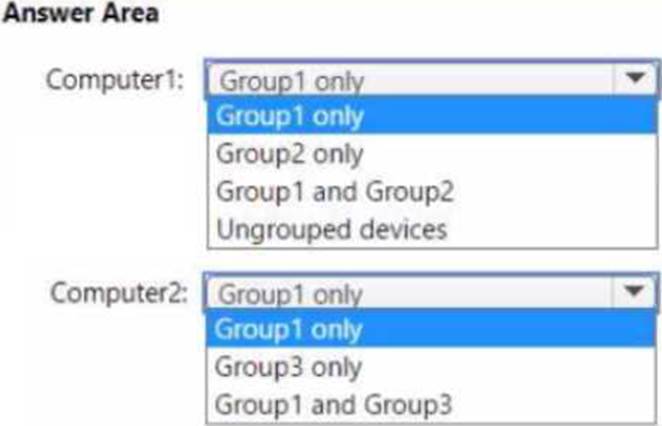
Of which groups are Computer! and Computed members? To answer, select the appropriate options in The answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
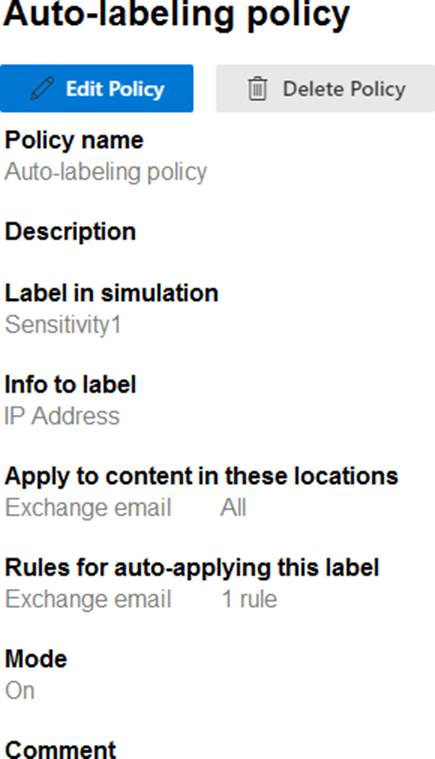
You have a Microsoft 365 E5 tenant.
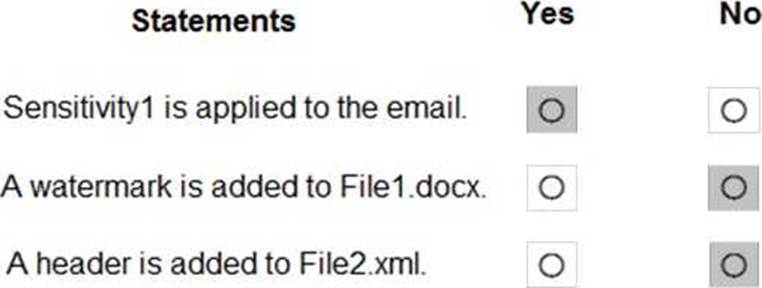
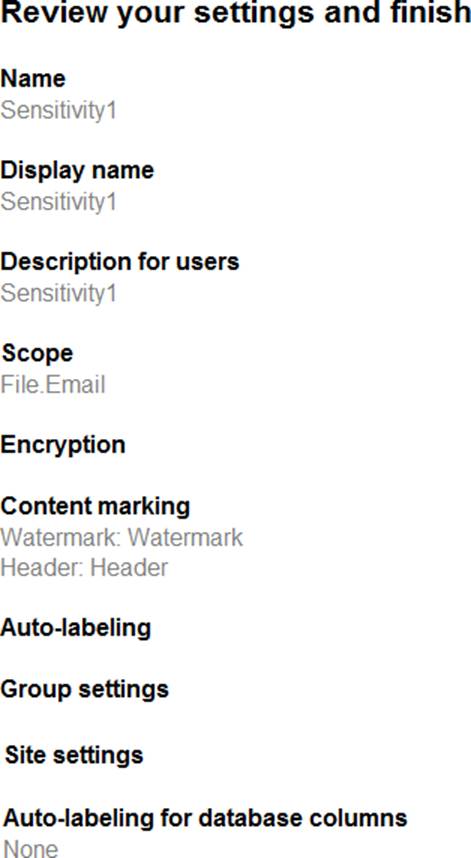
You have a sensitivity label configured as shown in the Sensitivity label exhibit. (Click the Sensitivity
label tab.)
You have an auto-labeling policy as shown in the Auto-labeling policy exhibit. (Click the Auto-labeling policy tab.)
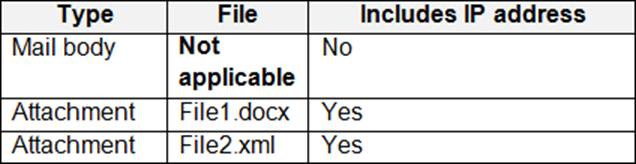
A user sends an email that contains the components shown in the following table.
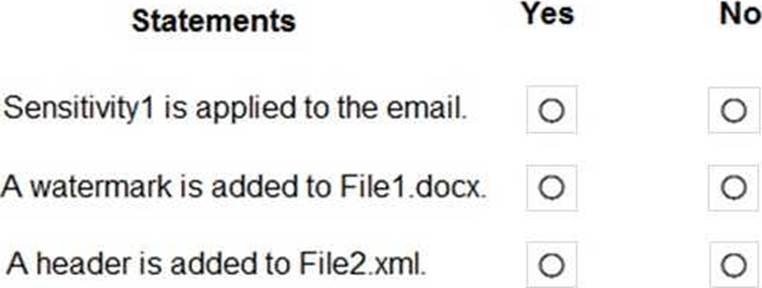
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant that contains a Windows 10 device named Device1 and the Microsoft Endpoint Manager policies shown in the following table.
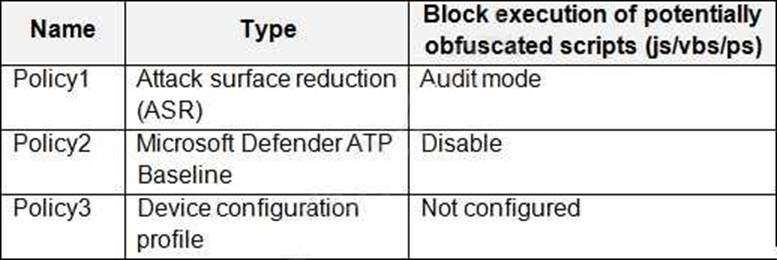
The policies are assigned to Device1.
Which policy settings will be applied to Device1?
- A . only the settings of Policy1
- B . only the settings of Policy2
- C . only the settings of Policy3
- D . no settings
HOTSPOT
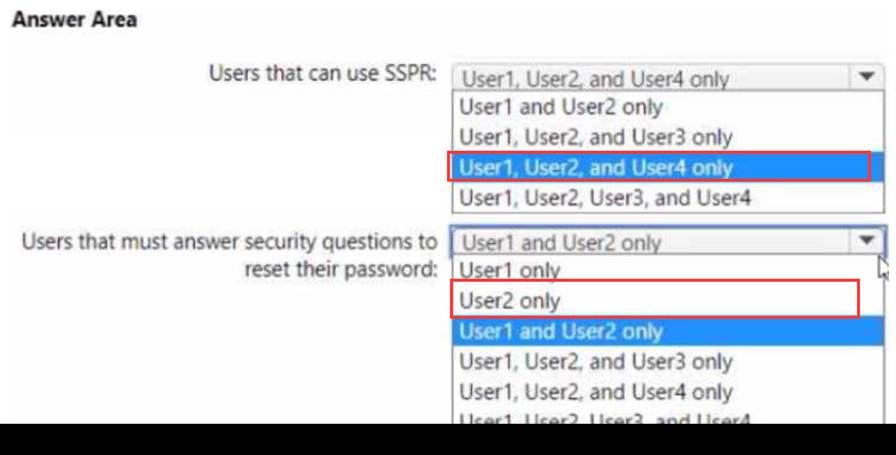
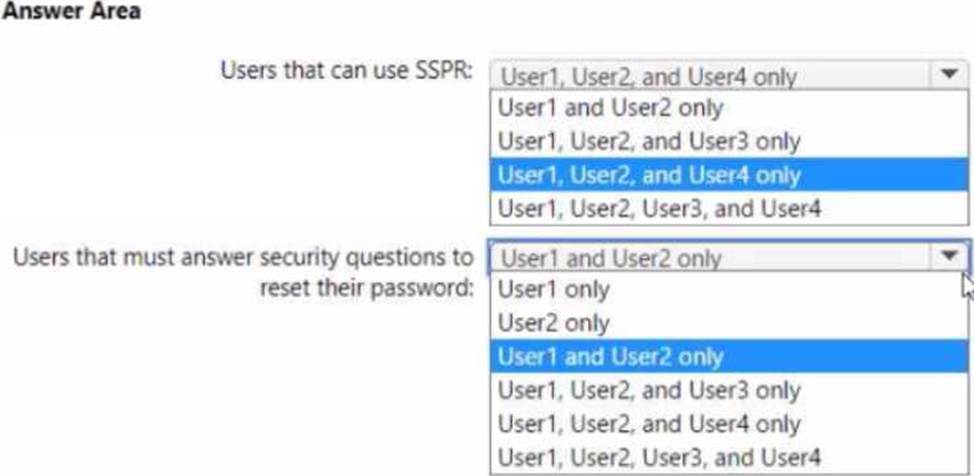
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
You enable self-service password reset (SSPR) for Group1. You configure security questions as the only authentication method for SSPR.
Which users can use SSPR, and which users must answer security questions to reset their password? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
Which role should you assign to User1?
Available Choices (select all choices that are correct)
- A . Hygiene Management
- B . Security Reader
- C . Security Administrator
- D . Records Management
Which role should you assign to User1?
Available Choices (select all choices that are correct)
- A . Hygiene Management
- B . Security Reader
- C . Security Administrator
- D . Records Management
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
From Microsoft Defender for Endpoint you turn on the Allow or block file advanced feature.
You need to block users from downloading a file named File1.exe.
What should you use?
- A . an indicator
- B . a suppression rule
- C . a device configuration profile
You have a Microsoft 365 IS subscription and use Microsoft Defender for Cloud Apps. You register a cloud app named App1 in Microsoft Entra 10. You need to create an access policy for Appl.
What should you do first?
- A . Configure an app connector to Defender for Cloud Apps.
- B . Add a security Information and event management (SlEM) agent to Defender for Cloud Apps.
- C . Create an app tag for App 1.
- D . Deploy Conditional Access AppControl toApp 1.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it as a result these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities.
The solution must meet the following requirements:
• Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
• User passwords must be 10 characters or more.
Solution: Implement pass-through authentication and configure password protection in the Azure AD tenant.
Does this meet the goal?
- A . Yes
- B . No