Microsoft MS-102 Übungsprüfungen
Zuletzt aktualisiert am 02.02.2026- Prüfungscode: MS-102
- Prüfungsname: Microsoft 365 Administrator
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 02.02.2026
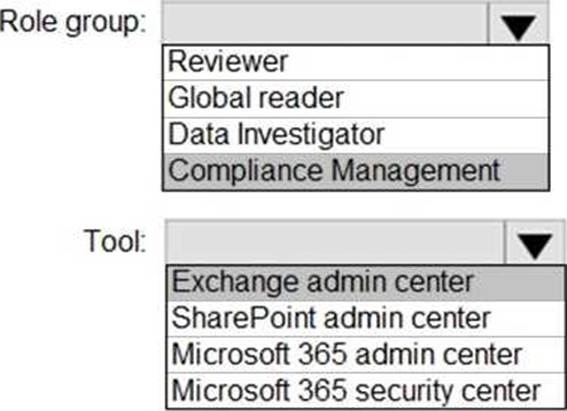
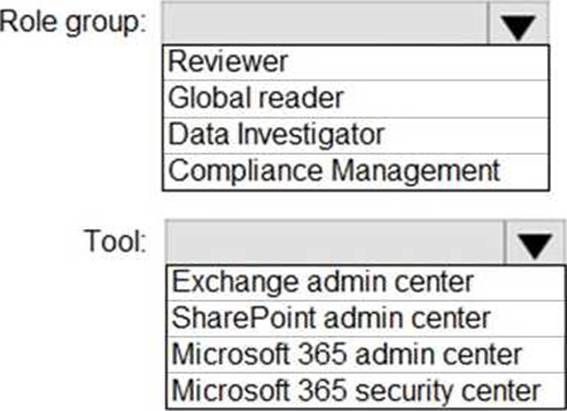
HOTSPOT
You need to ensure that User2 can review the audit logs. The solutions must meet the technical requirements.
To which role group should you add User2, and what should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your network contains three Active Directory forests. There are forests trust relationships between the forests.
You create an Azure AD tenant.
You plan to sync the on-premises Active Directory to Azure AD.
You need to recommend a synchronization solution. The solution must ensure that the synchronization can complete successfully and as quickly as possible if a single server fails.
What should you include in the recommendation?
- A . one Azure AD Connect sync server and one Azure AD Connect sync server in staging mode
- B . three Azure AD Connect sync servers and one Azure AD Connect sync server in staging mode
- C . six Azure AD Connect sync servers and three Azure AD Connect sync servers in staging mode
- D . three Azure AD Connect sync servers and three Azure AD Connect sync servers in staging mode
You have a Microsoft 365 subscription that contains a user named User1.
User1 requires admin access to perform the following tasks:
Manage Microsoft Exchange Online settings.
Create Microsoft 365 groups.
You need to ensure that User1 only has admin access for eight hours and requires approval before the role assignment takes place.
What should you use?
- A . zure AD Identity Protection
- B . Microsoft Entra Verified ID
- C . Conditional Access
- D . Azure AD Privileged Identity Management (PJM)
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Office 365 and contains a user named User1.
User1 emails a product catalog in the PDF format to 300 vendors. Only 200 vendors receive the email message, and User1 is blocked from sending email until the next day.
You need to prevent this issue from reoccurring.
What should you configure?
- A . anti-spam policies
- B . Safe Attachments policies
- C . anti-phishing policies
- D . anti-malware policies
You have a Microsoft E5 subscription.
You need to ensure that administrators who need to manage Microsoft Exchange Online are assigned the Exchange Administrator role for five hours at a time.
What should you implement?
- A . Azure AD Privileged Identity Management (PIM)
- B . a conditional access policy
- C . a communication compliance policy)
- D . Azure AD Identity Protection
- E . groups that have dynamic membership
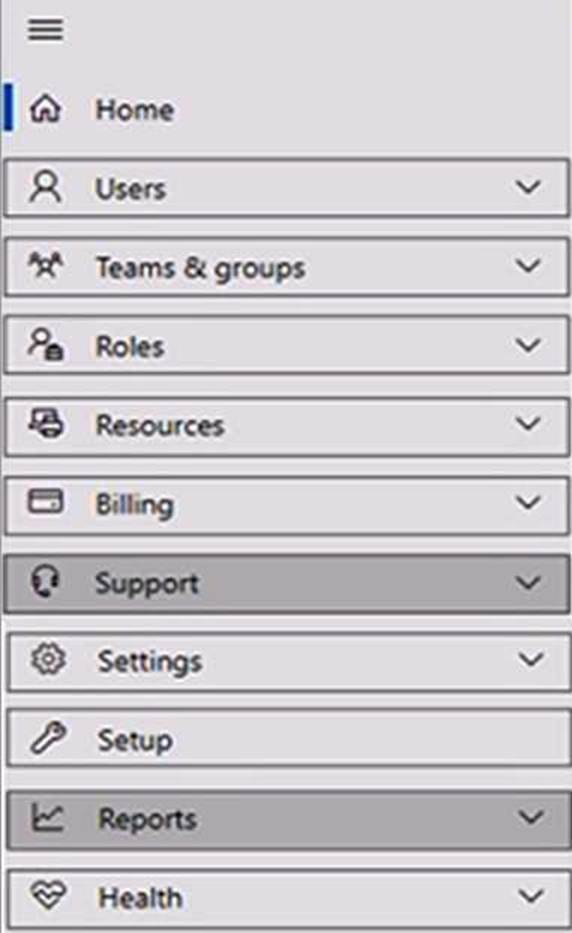
HOTSPOT
Your company has a Microsoft 365 E5 subscription.
You need to perform the following tasks:
View the Adoption Score of the company.
Create a new service request to Microsoft.
Which two options should you use in the Microsoft 365 admin center? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains a user named User1.
You need to ensure that User1 can search the Microsoft 365 audit logs from the Security & Compliance admin center.
Which role should you assign to User1?
- A . View-Only Audit Logs in the Security & Compliance admin center
- B . View-Only Audit Logs in the Exchange admin center
- C . Security reader in the Azure Active Directory admin center
- D . Security Reader in the Security & Compliance admin center
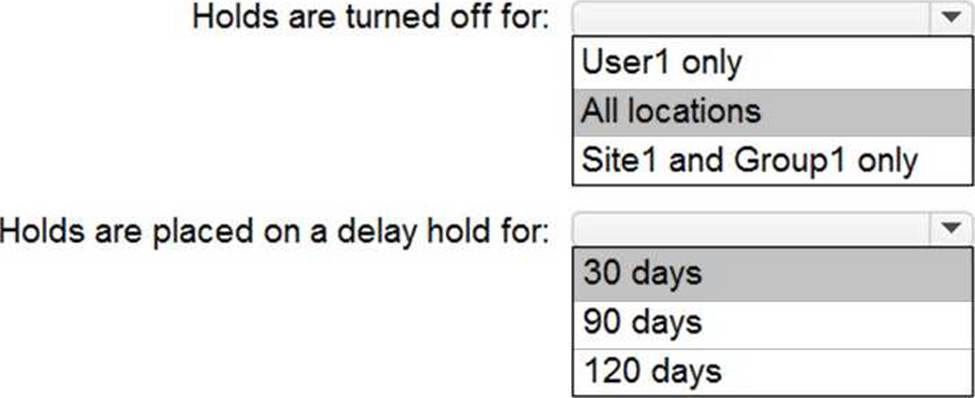
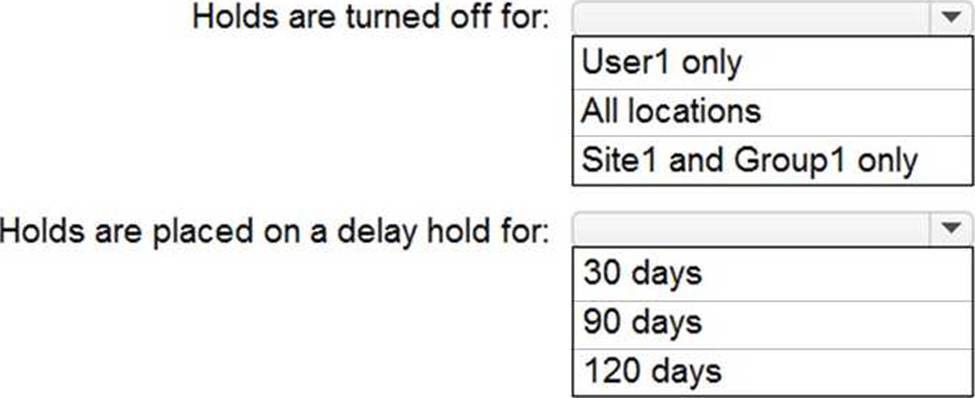
HOTSPOT
You have a Microsoft 365 E5 subscription that includes the following active eDiscovery case:
Name: Case1
Included content: Group1, User1, Site1
Hold location: Exchange mailboxes, SharePoint sites, Exchange public folders
The investigation for Case1 completes, and you close the case.
What occurs after you close Case1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
On Monday, you create a new user named User1.
On Tuesday, User1 signs in for the first time and perform the following actions:
• Signs in to Microsoft Exchange Online from an anonymous IP address
• Signs in to Microsoft SharePoint Online from a device in New York City.
• Establishes Remote Desktop connections to hosts in Berlin and Hong Kong, and then signs in to SharePoint Online from the Remote Desktop connections
Which types of sign-in risks will Azure AD Identity Protection detect for User1?
- A . anonymous IP address only
- B . anonymous IP address and atypical travel
- C . anonymous IP address, atypical travel, and unfamiliar sign-in properties
- D . unfamiliar sign-in properties and atypical travel only
- E . anonymous IP address and unfamiliar sign-in properties only
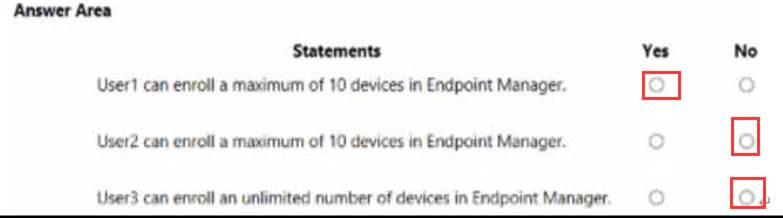
HOTSPOT
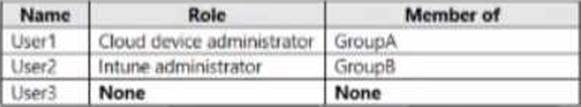
You have several devices enrolled in Microsoft Endpoint Manager
You have a Microsoft Azure Active Directory (Azure AD) tenant that includes the users shown In the following table.
The device limit restrictions in Endpoint manager are configured as shown in the following table.
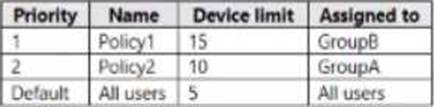
You add user as a device enrollment manager in Endpoint manager
For each of the following statements, select Yes if the statement is true. Otherwise, select No