Palo Alto Networks PCNSA Übungsprüfungen
Zuletzt aktualisiert am 08.03.2026- Prüfungscode: PCNSA
- Prüfungsname: Palo Alto Networks Certified Network Security Administrator
- Zertifizierungsanbieter: Palo Alto Networks
- Zuletzt aktualisiert am: 08.03.2026
You have been tasked to configure access to a new web server located in the DMZ. Based on the diagram what configuration changes are required in the NGFW virtual router to route traffic from the 10.1.1.0/24 network to 192.168.1.0/24?
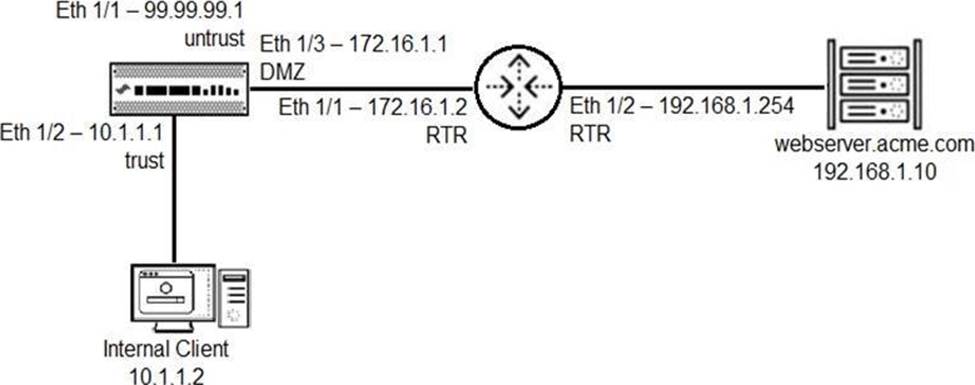
- A . Add a route with the destination of 192.168.1.0/24 using interface Eth 1/2 with a next-hop of 172.16.1.2.
- B . Add a route with the destination of 192.168.1.0/24 using interface Eth 1/3 with a next-hop of 192.168.1.10
- C . Add a route with the destination of 192.168.1.0/24 using interface Eth 1/3 with a next-hop of 172.16.1.2.
- D . Add a route with the destination of 192.168.1.0/24 using interface Eth 1/3 with a next-hop of 192.168.1.254.
Based on the screenshot, what is the purpose of the group in User labelled "it"?
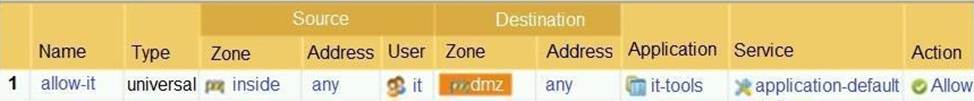
- A . Allows "any" users to access servers in the DMZ zone.
- B . Allows users to access IT applications on all ports.
- C . Allow users in group "it" to access IT applications.
- D . Allow users in group "DMZ" to access IT applications.
Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources?
- A . Windows-based agent deployed on the internal network
- B . PAN-OS integrated agent deployed on the internal network
- C . Citrix terminal server deployed on the internal network
- D . Windows-based agent deployed on each of the WAN Links
In order to protect users against exploit kits that exploit a vulnerability and then automatically download malicious payloads, which Security profile should be configured?
- A . Anti-Spyware
- B . WildFire
- C . Vulnerability Protection
- D . Antivirus
In order to protect users against exploit kits that exploit a vulnerability and then automatically download malicious payloads, which Security profile should be configured?
- A . Anti-Spyware
- B . WildFire
- C . Vulnerability Protection
- D . Antivirus
Which statement is true regarding a Heatmap report?
- A . When guided by authorized sales engineer, it helps determine the areas of greatest security risk
- B . It runs only on firewalls.
- C . It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
- D . It provides a percentage of adoption for each assessment area.
Which update option is not available to administrators?
- A . New Spyware Notifications
- B . New URLs
- C . New Application Signatures
- D . New Malicious Domains
- E . New Antivirus Signatures
Which link in the web interface enables a security administrator to view the security policy rules that match new application signatures?
- A . Review Apps
- B . Review App Matches
- C . Pre-analyze
- D . Review Policies
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
- A . User identification
- B . Filtration protection
- C . Vulnerability protection
- D . Antivirus
- E . Application identification
- F . Anti-spyware
What can be achieved by disabling the Share Unused Address and Service Objects with Devices setting on Panorama?
- A . Increase the per-firewall capacity for address and service objects
- B . Reduce the configuration and session synchronization time between HA pairs
- C . Increase the backup capacity for configuration backups per firewall
- D . Reduce the number of objects pushed to a firewall
