Palo Alto Networks PCNSA Übungsprüfungen
Zuletzt aktualisiert am 08.03.2026- Prüfungscode: PCNSA
- Prüfungsname: Palo Alto Networks Certified Network Security Administrator
- Zertifizierungsanbieter: Palo Alto Networks
- Zuletzt aktualisiert am: 08.03.2026
An administrator would like to create a URL Filtering log entry when users browse to any gambling website.
What combination of Security policy and Security profile actions is correct?
- A . Security policy = drop, Gambling category in URL profile = allow
- B . Security policy = deny. Gambling category in URL profile = block
- C . Security policy = allow, Gambling category in URL profile = alert
- D . Security policy = allow. Gambling category in URL profile = allow
An administrator would like to create a URL Filtering log entry when users browse to any gambling website.
What combination of Security policy and Security profile actions is correct?
- A . Security policy = drop, Gambling category in URL profile = allow
- B . Security policy = deny. Gambling category in URL profile = block
- C . Security policy = allow, Gambling category in URL profile = alert
- D . Security policy = allow. Gambling category in URL profile = allow
What do Dynamic User Groups help you to do?
- A . create a policy that provides auto-remediation for anomalous user behavior and malicious activity
- B . create a dynamic list of firewall administrators
- C . create a QoS policy that provides auto-remediation for anomalous user behavior and malicious activity
- D . create a policy that provides auto-sizing for anomalous user behavior and malicious activity
Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone. Complete the security policy to ensure only Telnet is allowed. Security Policy: Source Zone: Internal to DMZ Zone services "Application defaults", and action = Allow
- A . Destination IP: 192.168.1.123/24
- B . Application = `Telnet‘
- C . Log Forwarding
- D . USER-ID = `Allow users in Trusted‘
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
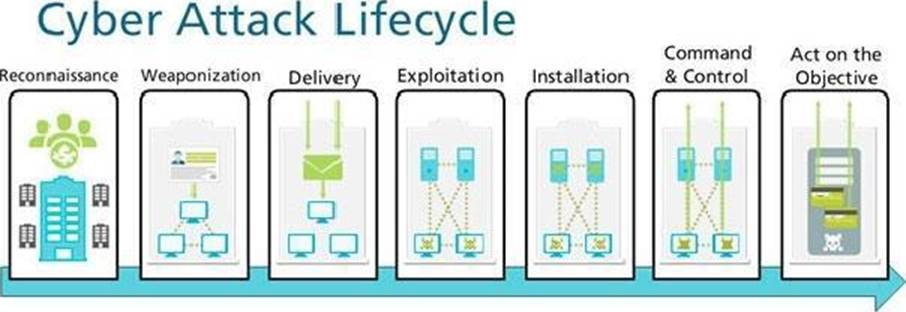
- A . Exploitation
- B . Installation
- C . Reconnaissance
- D . Act on Objective
According to best practices, how frequently should WildFire updates he made to perimeter firewalls?
- A . every 10 minutes
- B . every minute
- C . every 5 minutes
- D . in real time
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
- A . override
- B . allow
- C . block
- D . continue
All users from the internal zone must be allowed only Telnet access to a server in the DMZ zone.
Complete the two empty fields in the Security policy rules that permits only this type of access. (Choose two.)
Source Zone: Internal
Destination Zone: DMZ Zone
Application: __________?
Service: __________?
Action: allow
- A . Service = "application-default"
- B . Service = "service-telnet"
- C . Application = "Telnet"
- D . Application = "any"
What is an advantage for using application tags?
- A . They are helpful during the creation of new zones
- B . They help with the design of IP address allocations in DHCP.
- C . They help content updates automate policy updates
- D . They help with the creation of interfaces


