Palo Alto Networks PCNSE Übungsprüfungen
Zuletzt aktualisiert am 08.03.2026- Prüfungscode: PCNSE
- Prüfungsname: Palo Alto Networks Certified Network Security Engineer Exam
- Zertifizierungsanbieter: Palo Alto Networks
- Zuletzt aktualisiert am: 08.03.2026
Which two statements correctly describe Session 380280? (Choose two.)

- A . The session went through SSL decryption processing.
- B . The session has ended with the end-reason unknown.
- C . The application has been identified as web-browsing.
- D . The session did not go through SSL decryption processing.
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group.
What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
- A . A service route to the LDAP server
- B . A Master Device
- C . Authentication Portal
- D . A User-ID agent on the LDAP server
An engineer reviews high availability (HA) settings to understand a recent HA failover event.
Review the screenshot below.
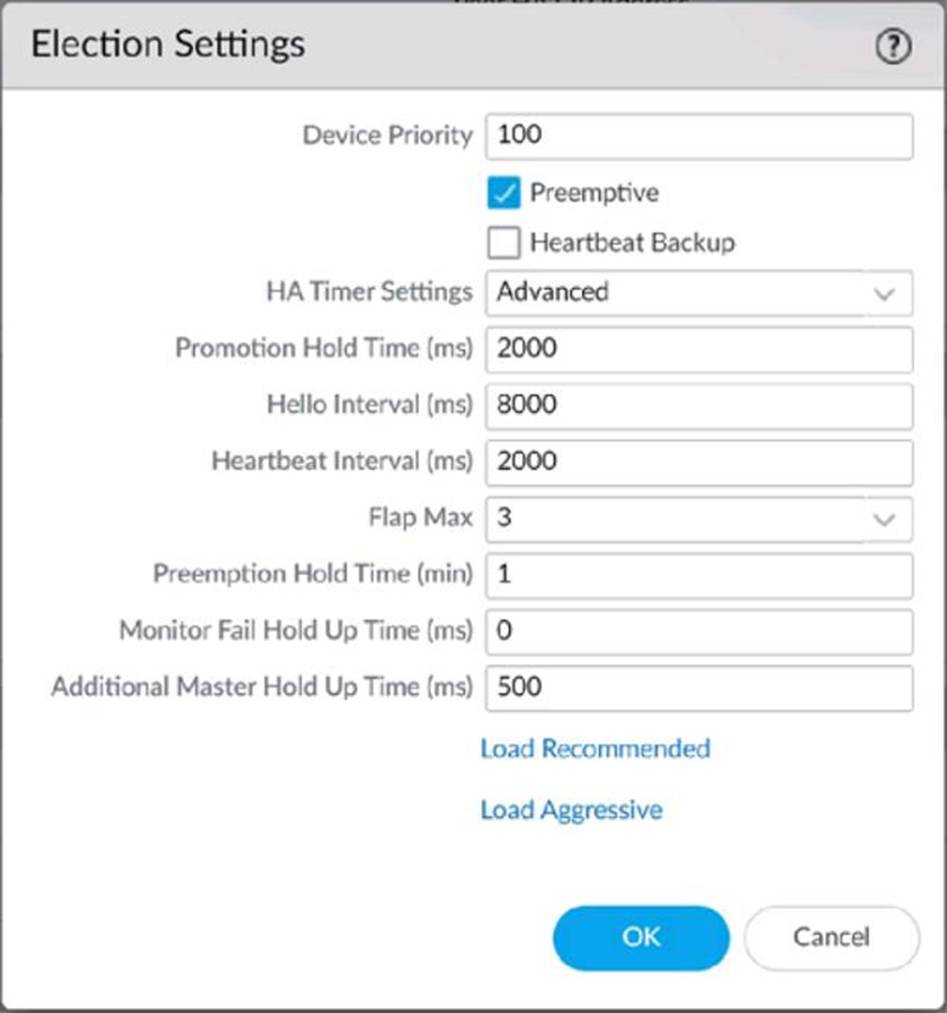
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
- A . Hello Interval
- B . Promotion Hold Time
- C . Heartbeat Interval
- D . Monitor Fail Hold Up Time
Given the following snippet of a WildFire submission log did the end-user get access to the requested information and why or why not?
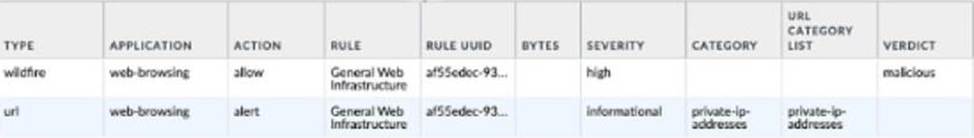
- A . Yes, because the action is set to alert
- B . No, because this is an example from a defeated phishing attack
- C . No, because the severity is high and the verdict is malicious.
- D . Yes, because the action is set to allow.
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
- A . No Direct Access to local networks
- B . Tunnel mode
- C . iPSec mode
- D . Satellite mode
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
- A . A Deny policy for the tagged traffic
- B . An Allow policy for the initial traffic
- C . A Decryption policy to decrypt the traffic and see the tag
- D . A Deny policy with the "tag" App-ID to block the tagged traffic
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
- A . Only one vsys or one firewall can be assigned to a device group, and a multi-vsys firewall can have each vsys in a different device group.
- B . Multiple vsys and firewalls can be assigned to a device group, and a multi-vsys firewall can have each vsys in a different device group.
- C . Only one vsys or one firewall can be assigned to a device group, except for a multi-vsys firewall, which must have all its vsys in a single device group.
- D . Multiple vsys and firewalls can be assigned to a device group, and a multi-vsys firewall must have all its vsys in a single device group.
A security engineer needs firewall management access on a trusted interface.
Which three settings are required on an SSL/TLS Service Profile to provide secure Web UI authentication? (Choose three.)
- A . Minimum TLS version
- B . Certificate
- C . Encryption Algorithm
- D . Maximum TLS version
- E . Authentication Algorithm
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
- A . Resource Protection
- B . TCP Port Scan Protection
- C . Packet Based Attack Protection
- D . Packet Buffer Protection
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security
certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
- A . A web server certificate signed by the organization’s PKI
- B . A self-signed certificate generated on the firewall
- C . A subordinate Certificate Authority certificate signed by the organization’s PKI
- D . A web server certificate signed by an external Certificate Authority
